Table of contents
Open Table of contents
Intro
In this article, I will share my experience with eCPPTv3. It is the third version of the eCPPT certification, available since June. I expected it to be an improvement over the previous version, but that was not the case. I believe there are better ways to spend your money than purchasing a voucher for this exam. Yes, I am going to criticize the eCPPTv3.
Additionally, I will share what helped me prepare for the exam, what caused me to fail on my first try, what I didn’t like, and what I did like.
My Experience
As the exam format is new, it is hard to find any information about what to expect. I believe there will be more information available later, but at the moment, I feel like I am one of the first to share it. With no information available besides official sources, I couldn’t be sure if I was adequately prepared or if the official training was sufficient.
It was a complete black box for me, and I ambitiously failed my first attempt. I realized I was not fully prepared and that the official training was not enough. Additionally, the exam itself had some flaws that hindered my potential result.
However, on my second try, I successfully passed the exam!
Positive Side
There are many things I disliked, so I’ll start with the positives. :)
- I learned and gained valuable experience on how to pentest Active Directory (AD).
- There were no spoilers about the exam, making it much more interesting. (This might not be the case in the future.)
- The 24-hour timeframe means you get your exam results earlier, which is a big plus for me, as I’m impatient.
I think that’s all.
Negative Sides and my Advice
There will be many things to criticize. I am not doing this to harm INE or complain about the difficulties I faced. My goal is to warn you about what to expect and to encourage INE to improve the certification. The issues I will share were also shared to INE during the exam (as of this publication, there has been no response). Additionally, some of these issues might be unique to my exam experience.
I will also offer some advice to help mitigate these issues.
The Training is not enough
The Problem
You cannot adequately prepare for the exam using only the content and labs provided by INE, especially the Active Directory (AD) portion. For an exam primarily focused on Active Directory, the training offered was almost nonexistent. This was one of the main reasons I failed the first time. To pass, you need to learn from other sources and gain additional hands-on experience on other platforms as well!
Training I chose
I had some prior knowledge related to pentesting Linux and Windows machines that I gained from TryHackMe, TCM, INE (eJPT and eWPT trainings), and exploring the internet. This background helped me easily hack the Linux host(s) in the network. While the eCPPTv3 training provided some additional help, it was not sufficient without prior knowledge.
After failing my first attempt, I realized I needed to improve my AD pentesting skills. Hack The Box was extremely helpful! I purchased subscriptions for both their Academy and CTF platforms.
HTB Academy modules that were more than enough for the AD part of the exam:
- Introduction to Active Directory
- Windows Attacks & Defense (The attack part)
- Active Directory Enumeration & Attacks (complete it fully)
- Pivoting, Tunneling, and Port Forwarding (I completed the half of this)
HTB CTF Track - Active Directory 101: I solved easy and medium CTFs before retaking the exam, which helped a lot as well.
If you have issues with web exploitation, Linux machine exploitation, or working with public exploits, don’t worry. These parts of the exam were at the level of THM CTF medium-hard or HTB CTF easy.
Exam Environment
The provided exam environment was not very comfortable to work with. It would have been better to have a VPN connection instead of a web interface to the attack machine, as the web interface negatively affected network connectivity and speed. Additionally, when I first used Firefox to access the Guacamole client, the copy-paste feature did not work. After losing some time with this issue, I switched to Google Chrome.
Reset
The Lab Reset feature seems not to be working properly. Firstly, after a reset, you need to wait 5-10 minutes for the lab to start, which is a significant amount of time. Secondly, I experienced serious issues related to lab resets. During my first attempt, after a reset, I could not find a flag that should have been in a certain place. On my second attempt, I did not reset the lab at all, and the flag was there. This issue severely affected my exam results during my first attempt. Afterward, I reported the issue to INE, and they acknowledged it but insisted that “everything is perfect, the exam has no flaws.”
Flaws
There was an issue that I can’t disclose and that may not be particularly useful to know about. It might have been unique to my experience. In 2-3 questions, I couldn’t find the required information even though I had system-wide access to a host. For example, if X was required to be found, and there was a guaranteed way to find it, it simply wasn’t present on the system (similar to the flag issue mentioned above).
Another issue is that the submission of some answers is not very clear. For example, when required to submit a found username, the answer input is case-sensitive. The username can be found in different places in various formats, such as elnur_badalov, elnur badalov, and ELNUR_BADALOV. It’s unclear which format should be submitted.
And there were some other issues too.
Certified Password Sprayer
Wordlists
The wordlists recommended in the exam guide are not good.
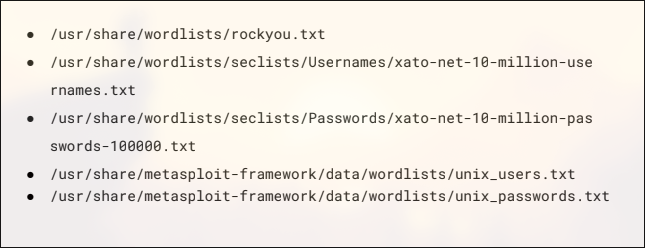 I strongly recommend using the following wordlists:
I strongly recommend using the following wordlists:
common_corporate_passwords.lst
seasons.txt
months.txt
xato-net-10-million-passwords-10000.txt
rockyou.txt
Brute Force not Password Spray
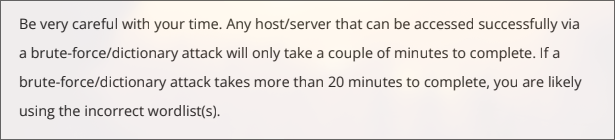
Password spray involves using a single password for a list of users. In the exam, you use a list of passwords for a list of users. And yes, the found password is weak, but there are tons of weak passwords.
A lot
I was brute-forcing extensively to find anything. It’s like password.lst multiplied by username.lst multiplied by services.lst multiplied by hosts.lst times.
The following statement is a lie:
Toolset
I would like to share tools/commands I used during the exam:
- AD enum/brute force/password spray/access
kerbrutecrackmapexecevil-winrm(in my case it was not working on the attack machine)xfreerdpbloodhound-pythonsmbclientrpcclient- Windows built-in
runasEnter-PSSessionnet
- Powershel Scripts
powerview.ps1powerup.ps1winpeas.ps1
- Metasploit
msfvenommsfconsoleexploit/windows/misc/hta_serverfor getting ameterpretershell
meterpreterkiwihashdumpcreds_alllsa_dump_secretslsa_dump_sam
getsystem
- Impacket
GetNPUserspsexecwmiexec
- Others
wpscanhydrahashcatfpingnmap
- GTFObins
Note Taking
Lastly, I would like to share an obvious tip:
- Take notes! You need to pentest quite a big infrastructure, and there a lot information.
- Keep every command you run! You may reuse them.
- Keep every piece of information you find! It may become valuable later.
- Keep everything organized!
The last point is the hardest part. I used Obsidian software for note-taking, and it worked well for me.
Folder Structure
- General
- Credentials
- Hosts
- NMAP Scan and Host Discovery
- AD
- Domain Info
- Users
- User1
- User2
- Brute Force
- Linux-Host-1
- Linux-Host-2
- Windows-Host-1 or its name in the domain (like DC01)
Note Structure
In the Credentials note, I keep information about every hash and credential I find. I use the following table:
| User (source) | Password | Authenticates | Type of user |
|---|---|---|---|
| elnur (spray) | asdasdasd | Linux-Host-1 | not sudoer |
| administrator (lsa_dump_secrets) | 123qwe123 | DC01 | local |
| badalov (asrep or kerberoast) | Welcom1 | SomeDomain | can rdp to DC01 |
In the Hosts note:
- My machine’s IP
- Scope
- Hosts
| host | ip | Linked Note |
|---|---|---|
| DC01.somedomain.com | x.x.x.x | |
| linux-host-1 | x.x.x.y |
- Services to check
| host | service |
|---|---|
| linux-host-1 | - port - service name - port - service name |
| DC01.somedomain.com | - port - service name - port - service name |
- Shares
| host | share |
|---|---|
| DC01.somedomain.com | Share1(R), Share2(R,W) |
In Domain Info, I record any general information about the domain, such as BloodHound or PowerView results.
In Brute Force, I keep track of username lists, password lists that are in progress or checked out, services to check out, and commands to run.
In Users and Host notes, I store information specific to each user or host.
Conclusion
In summary, the eCPPTv3 exam presents significant challenges, partly due to the insufficient training materials and the technical issues within the exam environment. My experience highlighted the need for additional preparation beyond the provided resources, particularly in Active Directory pentesting. Utilizing external platforms like Hack The Box was crucial for my success.
Despite the obstacles, my journey through the eCPPTv3 exam was ultimately rewarding. It underscored the importance of thorough preparation, strategic note-taking, and adaptability. While there are many areas for improvement in the current exam setup, I hope that my feedback and experiences will help future candidates better navigate these challenges and encourage INE to enhance the certification process.
Remember, persistence and a proactive approach to learning are key. Even if you fail, you will have additional two weeks to improve, consider nuances and retake the exam. Good luck to all future candidates!
If you have any questions, feel free to contact me on LinkedIn.